 Explained: Bitcoin 51% Attacks
Explained: Bitcoin 51% Attacks 
Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
One of the worst things to happen to a proof-of-work cryptocurrency is a 51 percent attack. Such attacks undermine the immutability—and consequently the trust—in a blockchain.
Satoshi Nakamoto summarized proof-of-work as “one-CPU-one-vote.” Since then, the cryptocurrency mining industry has advanced beyond CPU mining, which could compute the Bitcoin algorithm thousands of times per second, to application-specific integrated circuits which can perform billions of computations. This hardware specialization tends to centralize over time and is only available to high-tech manufacturers.
Does that make it inevitable that every cryptocurrency will succumb to 51 percent attacks?
The Fundamentals of Proof-of-Work
Proof-of-work is the underlying algorithm theorized by the anonymous inventor of Bitcoin, Satoshi Nakamoto. In a proof-of-work system, participants (miners) use computer hardware to complete a difficult algorithm, the SHA-256 algorithm.

After this algorithm is solved, transaction data is bundled together for all transactions submitted within a window of approximately 10 minutes, called a block. The miner who finds the solution to the SHA-256 algorithm first is the one that gets to decide which block to include next in the chain. The longest chain of these solutions is the canonical, or ‘true’ version of the blockchain.
The hash rate (hashing power) of any piece of computer hardware is determined by the number of attempts it can make to solve this algorithm. The more attempts, the more likely the solution to the next block will be found.
Although Satoshi Nakamoto originally conceptualized “one-CPU-one-vote,” mining is now dominated by application-specific integrated circuits (ASICs), machines built specifically to solve the SHA-256 algorithm at lightning speed.
Details of a 51 Percent Attack
In Bitcoin and other cryptocurrencies, a 51 percent attack is possible if a single miner, or group of colluding miners (a cartel), can assemble more hashing power than all other mining participants. Advancement in ASICs aside, hashing power is roughly proportionate to how much money a miner is willing to spend on engineering research, hardware, and electricity.

If a situation arises where a group of miners have control of more than 50 percent of the total hashing power in a network, then that group could ‘outvote’ honest miners. As mentioned above, the canonical blockchain is always the longest chain based on Nakamoto’s rules. That means these malicious miners would statistically control who has the longest chain, and therefore determine which transactions to include on the blockchain.
This behavior is problematic because it invalidates one of the problems Bitcoin solves in normal conditions—double-spending—where a user attempts to spend the same Bitcoin multiple times.
Ramifications of an Attack
Once an attacker has assembled sufficient hashing power, Nakamoto describes two options:
“…[the miner] would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins.”
An attacker could defraud people through several methods. The attacker could create conflicting transactions, therefore refunding coins to themselves or someone else after a transaction. Or, the miners could mine empty blocks and simply invalid transactions, again returning coins to the attackers.
An example of how an attacker could profit from this is through targeting an exchange. After making a deposit and converting the attacker’s coins into another valuable cryptocurrency, the attacker could then refund the coins back to himself while retaining the illicitly gained crypto.
Assumption of Honesty
That said, Nakamoto argues that playing by Bitcoin’s rules is more profitable than attacking it:
“He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.”
Nakamoto is right that if someone were to conduct a 51 percent attack on Bitcoin, it would greatly reduce the value of coins, and consequently the profitability of any Bitcoin ASICs and any BTC holdings that attacker has.
Unfortunately, this only applies if Bitcoin—or any other cryptocurrency in question—is the leader in that particular mining algorithm. This applies to Ethereum’s Ethash, Zcash’s Equihash, or Litecoin’s Scrypt algorithms. Reuben Yap, the COO of Zcoin, effectively summarizes why this is the case:
“As an ASIC that can only do one thing [mine one particular crypto], it doesn’t make sense to attack the coin that gives my ASIC value. When I am invested in an ASIC, I am effectively investing in the coin family [and its algorithm].”
When Incentives Encourage Attacks
There is a situation that arises when a cryptocurrency uses a particular algorithm while not controlling the majority of hashing power within that algorithm. For example, there are dozens of cryptos that use Bitcoin’s SHA-256 PoW algorithm. Competitors that use that same algorithm are vulnerable.

When a situation arises where there are incentives to undermine a competitor, attacks follow. For example, during the Bitcoin Cash Hash Wars, when two forks (ABC and S.V.) of BCH formed, miners of each fork used their hashing power to actively undermine the stability of their competitor.
There are other instances where a 51 percent attack becomes rational behavior. Mark Nesbitt, a security engineer at Coinbase, details how Vertcoin endured four attacks:
“In four distinct incidents, the latest of which concluded on 12/2 [Dec. 2nd], Vertcoin (VTC) experienced 22 deep chain reorganizations, 15 of which included double spends of VTC. We estimate that these attacks could have resulted in the theft of over $100,000. The largest reorg. was over 300 blocks deep.”
Vertcoin uses the Lyra2RE mining algorithm. The problem arises when miners in this algorithm family can choose from a number of different, profitable projects to mine, including Verge, Monacoin, and others. If users of Vertcoin are defrauded of their funds, that doesn’t substantially undermine the value and the profit-making potential of those Lyra2RE ASICs.
Manipulating Immutability
There are several ways that an attacker could manipulate the blockchain to conduct an attack. To understand these methods, first, it is necessary to look at another supposed characteristic of a blockchain: immutability.
Immutability arises when the likelihood of a transaction getting reversed is next to impossible. The reason for this is the same reason there are ‘confirmation times’ or ‘number of confirmations’ before vendors consider a transaction valid. As said by Nakamoto:
“To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes… the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added.”
Based on that fact, the chance of a transaction getting reversed by malicious actors, or by mere chance, decreases exponentially as more time passes and blocks are added to the chain.
Even in normal conditions, sometimes transactions are invalidated because of this process. If one group of miners finds the correct solution to the Bitcoin algorithm, and another group finds one soon after, it requires a tie-breaker (another block) to determine which chain is the canonical (true) version of Bitcoin. The block that is not chosen is then said to be ‘orphaned,’ with those transactions considered invalid.
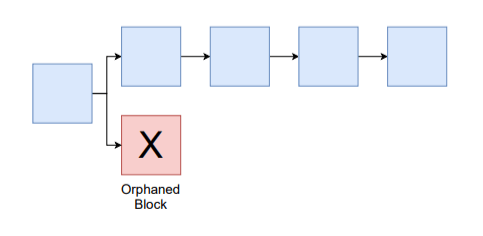
Once a transaction has had a sufficient number, with five to ten being a common number, of blocks mined on top of it, the chances of it getting reversed by mere chance become so infinitesimally small that it’s considered immutable. Unless, of course, there’s an attack.
How to Conduct an Attack
A malicious actor can conduct attacks in several different ways. The attacker could do this gradually, publishing newly found blocks and invalidating (orphaning) blocks found by other honest miners.
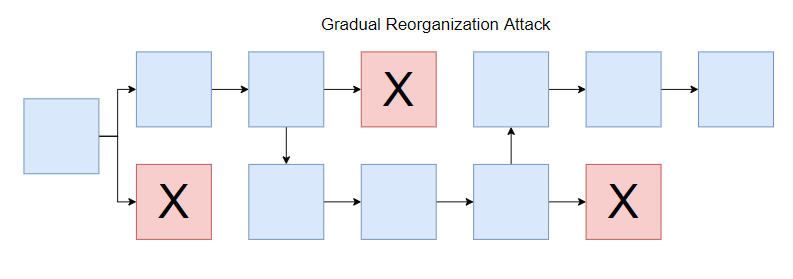
The attacker could also mine privately. In this case, the users of the network would assume everything is operating as usual. Then, the miner suddenly goes online and publishes a long string of valid blocks and invalidates a large number of transactions (called a reorganization or reorg.), replacing the old segment of the chain with the attacker’s new segment.
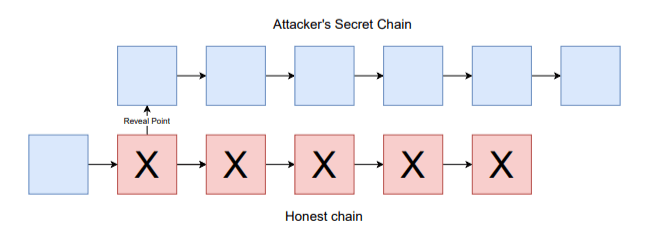
Profiteering from an Attack
Through this process, an attacker could profit in a few different ways. The miner could conduct transactions on the honest chain while simultaneously creating conflicting transactions on the attacker’s secret chain. Once published, the miner could revert those transactions or send it to another party.
These attacks can be performed on a large scale against a cryptocurrency exchange. By depositing coins into an exchange, the attacker could exchange at-risk coins, such as Vertcoin, for another valuable cryptocurrency.
Then, by conducting an attack, they could reverse those transactions and defraud participants on that exchange, returning those coins back to the attacker’s wallet. The attacker could repeat this process so long as the coins have value.
Or, the attacker could perform the same process above while mining ‘empty’ blocks, or blocks not containing any transactions. This would also revert funds back to the attacker by invalidating transactions that the attacker conducted on the honest chain. By invalidating blocks found by other miners, the miner could earn all of the mining rewards. In Bitcoin, this reward is currently 12.5 newly created BTC.
Another way to profit is by simply undermining the usability of a competitor’s blockchain. If a miner is a BTC holder, it might benefit that miner to cause long transaction delays and reverse transactions on a competitor, like BCH, which has less than 10 percent of the hashing power of Bitcoin. These BCH holders could then exchange their holdings for the more reliable BTC, causing that miner’s holdings to appreciate in value.
Centralization and the Ease of a 51 Percent Attack
The ease of a 51 percent attack is largely determined by the dollar-cost of overcoming a network’s total hash power (in hardware and electricity). Another factor is how centralized a network is, which factors into the ease of miner collusion.
On the Bitcoin network and other networks with ASIC hardware, mining over time naturally becomes more centralized. The process of creating advanced computer chips necessary to mine efficiently incur large research and development costs, and require multi-million—even billion dollar—chip manufacturing foundries.
The companies that create this hardware have to decide whether to keep or sell these ASICs. Unlike other computer chip producers, such as Intel, AMD, and Nvidia, it doesn’t make sense to hoard their own products. However, in the case of mining ASICs, each machine is practically a money-making device.

This encourages these large corporations to stockpile their own mining hardware, centralizing mining over time. As these participants amass more hashing power, it becomes easier to conduct attacks on the network, as it requires fewer and fewer participants to collude.
Currently, 70-80 percent of Bitcoin mining is conducted in China, while the manufacture of mining hardware is also controlled by several Chinese companies such as Bitmain and Bitfury. In another article, CryptoSlate conducted its own research and estimates that it would cost roughly $1.4 billion to stage a 51 percent attack on Bitcoin.
Bitcoin’s Safety
That said, even if these miners could amass 51 percent of the network’s hashing power, it would not make sense to attack Bitcoin (from a profit standpoint) so long as Bitcoin remains the dominant cryptocurrency in terms of the number of miners that can profitably mine it.
Overall, the risk of a 51 percent attack boils down to incentives. As long as the incentives of miners and users are aligned, a cryptocurrency will continue to remain secure. If those incentives are misaligned, then havoc may ensue.

















































































































