![Ethereum Network Under Assault: Gas Price Manipulation May Indicate Covert EOS Attack [INTERVIEW]](https://cryptoslate.com/wp-content/themes/cryptoslate-2020/imgresize/timthumb.php?src=https://cryptoslate.com/wp-content/uploads/2018/07/ethereum-attack-cover.jpg&w=70&h=37&q=75) Ethereum Network Under Assault: Gas Price Manipulation May Indicate Covert EOS Attack [INTERVIEW]
Ethereum Network Under Assault: Gas Price Manipulation May Indicate Covert EOS Attack [INTERVIEW] Ethereum Network Under Assault: Gas Price Manipulation May Indicate Covert EOS Attack [INTERVIEW]
![Ethereum Network Under Assault: Gas Price Manipulation May Indicate Covert EOS Attack [INTERVIEW]](https://cryptoslate.com/wp-content/uploads/2018/07/ethereum-attack-cover-768x274.jpg)
Photo by Jaak Horn on Unsplash
The Ethereum network is currently under heavy load as gas prices soar due to a flood of transactions. While Ethereum gas prices and transaction load typically fluctuates in accordance with market activity, a dramatic surge in suspicious transaction volume suggests that the Ethereum Network may be the target of a coordinated attack — with experts providing evidence that Ethereum competitor EOS could be to blame.
Over the last week, Ethereum gas prices skyrocketed beyond 80 Gwei, causing Ethereum transaction costs to rise. The astoundingly high gas prices are caused by a series of smart contracts that placed a significant load on the network, delaying transaction confirmation times.
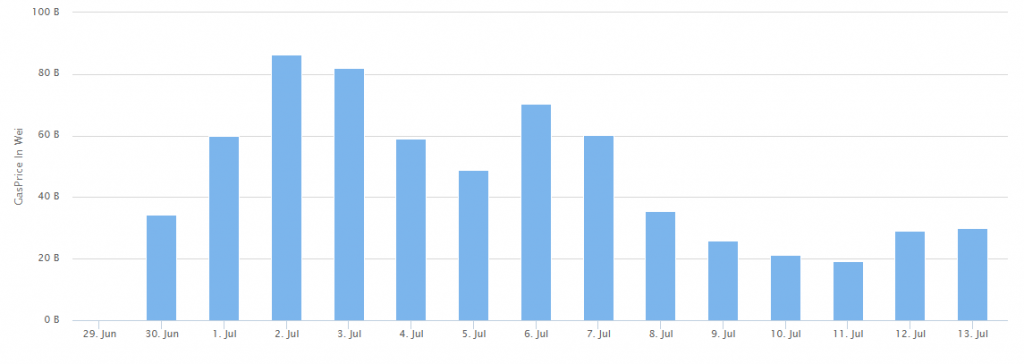
Ethereum transaction capacity has been heavily stressed recently due to the listing model used by Chinese cryptocurrency exchange FCoin, which has drawn criticism from the crypto community for flooding the Ethereum network with insignificant transactions.

A new investigation published by dApp developer Team JUST, however, delivered further insight into the cause of Ethereum network congestion. The Ethereum network, states Team JUST, is currently under attack, citing evidence of gas price manipulation driven by a series of network participants associated with Ethereum’s biggest competitor — EOS.
Ethereum Under Attack
In an announcement published July 14 via the Team JUST Discord, lead designer “Justo” outlined an analysis of the current state of the Ethereum network, highlighting a contract that, at the time of the report, was monopolizing 40% of Ethereum network capacity.
As a “beautiful and innovative copy-paste of a default ERC20 standard token called “IFishYunYu” with no features,” the token appears to do nothing.
“It seems tons of “unique” accounts are transferring massive volumes of this token constantly, almost 50 ETH of gas an hour have been steadily used for nearly 24 hours now. Just to transfer individual tokens to the Fcoin exchange. But of course. The exchange is just a red herring to distract you from what’s really happening.”
What is really happening, according to Team JUST lead developer Justo, is a malicious attack directed at the Ethereum network. Team JUST, a distributed app developer, is the team behind Fomo3D and P3D, the two highest volume games on the Ethereum network. The Ethereum network isn’t simply suffering under an onslaught of transaction spam caused by poor exchange listing practices, hypothesizes Justo, but is the target of a sustained corporate network attack executed by bot accounts funded directly by EOS.
“Airdrop” Tokens Spam Ethereum Network
In an interview with CryptoSlate, Justo broke down the evidence collected by Team JUST and their perspective on the relationship between Ethereum network congestion and potential EOS-driven interference:
“Team JUST is a decentralized application development team. We’ve been disappointed with EOS for a long while as it’s visibly been attacking the Ethereum network”
While there is no “smoking gun” demonstrating irrefutable proof that EOS is targeting Ethereum with a network attack, Justo cites a “culmination of evidence,” referencing a correlation between major EOS-related events and Ethereum gas price spikes:
“A good example is that we, as developers, had a release date that was approaching the release date of EOS. Gas prices, were 1-2 gwei, for months upon months. We predicted, accurately, that EOS would probably try to manipulate the ETH gas prices on the month up to its final mainnet release”
Team JUST highlights the serendipitous emergence of “airdrop” tokens delivered across the Ethereum network en masse and the EOS launch:
“Without fail, nearly two weeks before EOS released, multitudes of “Airdrop” tokens appeared out of nowhere. If you looked into these tokens the websites are absolutely laughable — rife with typos and copy-pasted bootstrap templates — but the tokens somehow had enough Ethereum to airdrop tens of thousands of dollars of gas-prices constantly for days on end”
EOS, states Justo, failed to set up a mainnet properly. The failure of the EOS project to obtain a majority vote in order to launch the EOS mainnet and other EOS issues, hypothesizes Team JUST, coincided with the release of new “airdrop” spam tokens in a predictable manner:
“Every time EOS had a failure 2-3 more “airdrop” tokens, appeared, shoved up the gas price for a day, and vanished”
Evidence Demonstrates EOS Used to Fund Airdrop Spam
Team JUST’s investigation focuses on the creator of the iFish contract that is currently absorbing nearly half of Ethereum network capacity. The creator of the contract minted almost 5 billion iFish tokens on July 3, 2018, then spread the newly-generated tokens across 10 separate addresses that then distributed the tokens to between 500-600 further addresses.
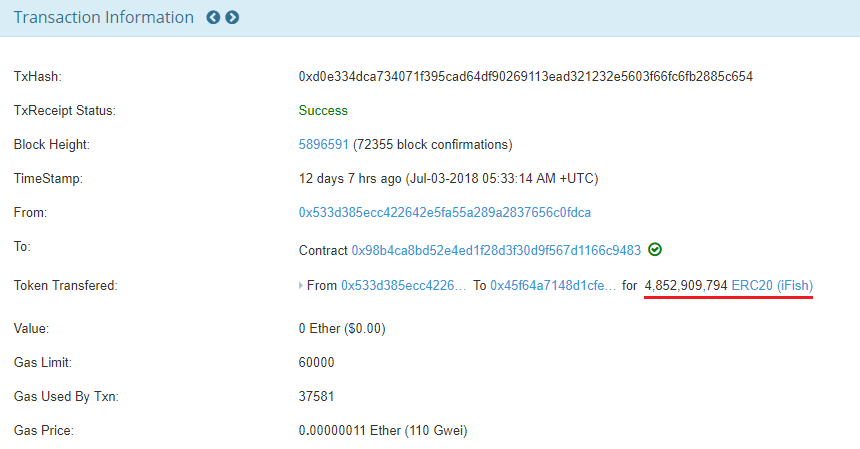
These addresses, states Team JUST, are the “mysterious” accounts that are spamming the Ethereum network:
“It’s one guy, it’s the creator of the token. He was doing it during the previous Fcoin exchange competition too. He’s running a multi-sided scheme.”
Interestingly, these addresses perform no function other than simply shuttling tokens between each other in order to create artificial volume, with bots running wash accounts:
“He even has bots running “wash” accounts … which is pretty cool, it just shoves the token into other accounts, and then those accounts shove it into other accounts, and then back to the big main account to simulate volume on the token itself. Try following a transaction, you’ll come right back to the big-daddy account.”
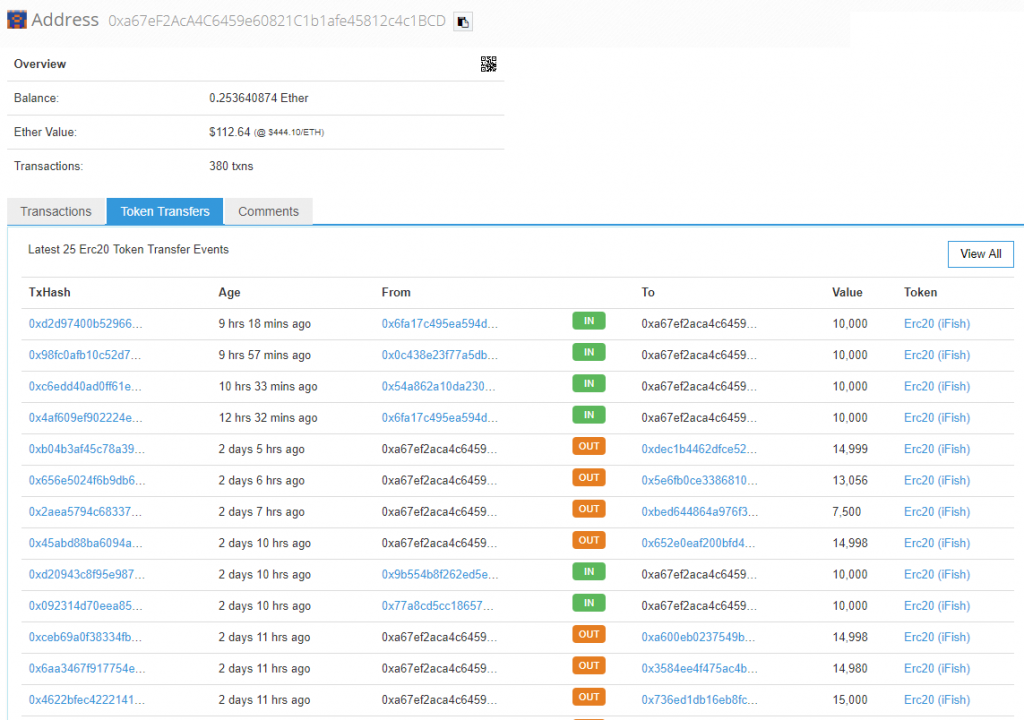
The fishiest element of the iFish spam mechanism, however, is the source of Ethereum with which the accounts fund the incredibly high gas fees required to execute the suspected attack.
Team JUST identified one of the accounts funding the process, locating a wallet that appears to receive large sums of EOS and then immediately markets sells them for ETH, which is then distributed out to contracts that subsequently use it to spam the Ethereum network.
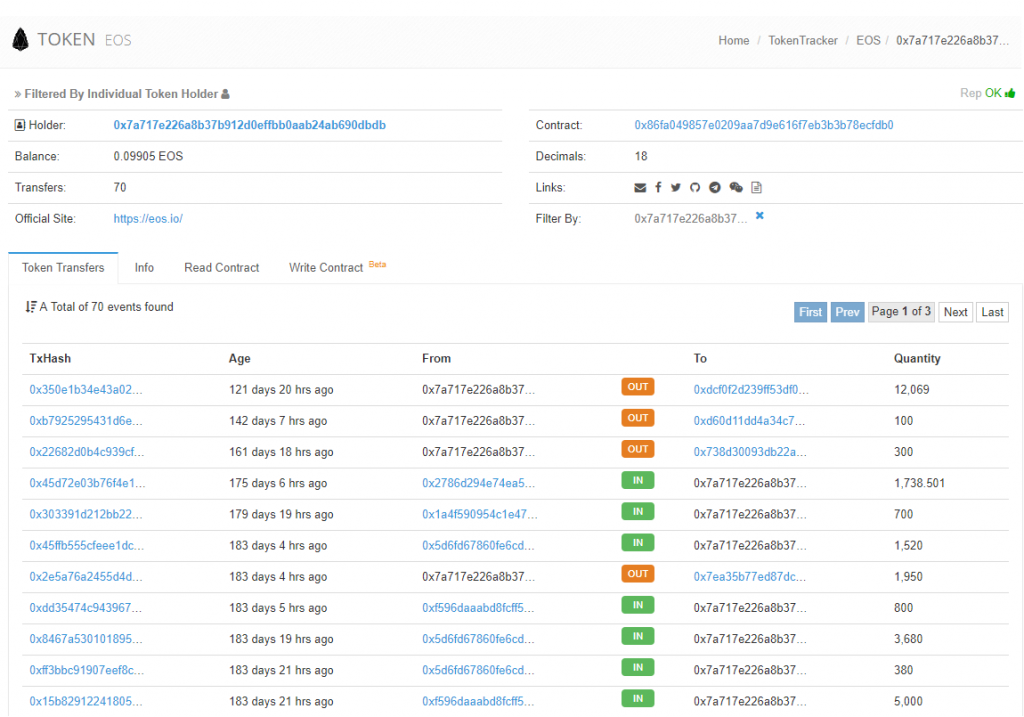
It’s not just the iFish token spamming the Ethereum network, however. Team Just has also identified HashFuture, which is currently absorbing 20% of the Ethereum network. HashToken is funded by a wallet that holds hundreds of ETH, which is connected to Nebulas. Several of the tokens on Nebulas, states Justo, lead back to the same wallet, which is directly linked to the accounts spamming the Ethereum network.
“The wallet that is distributing the iFish tokens has hundreds of eth in volume — literally incoming hundreds of thousands of dollars, outgoing hundreds of thousands of dollars. It’s very clearly not just some random guy with a token he made.”
The vast amounts of EOS used to fund the apparent Ethereum network attack, according to Justo, is evidence that EOS is responsible:
“If you had 2-3 million Ethereum, it was your biggest competitor, and you could manipulate it to make it look worse, would you? There is no other answer.”
EOS is “Destructive” to Cryptocurrency
Team JUST is no stranger to the EOS platform — the EOS RAM model states Justo, is a full clone of the team’s P3D project, which led to EOS requesting assistance from the team:
“We pioneered the bonded Ethereum token model where a smart contract holds the value of the token in Ethereum. Daniel Larimer seems to have taken it for EOS ram, and they didn’t understand the economics of it so it’s having a rough time. We had some (I think) developers reach out to us and ask us if we wanted to try to talk to EOS about fixing the EOS ram model.”
While Justo and Team JUST make it clear that they cannot guarantee that EOS.IO is “funding” the apparent attack, they are certain that many of the business practices they are applying are “very destructive to the cryptocurrency space.”
“We can say that consistently, there is a large amount of Ethereum and money from players with large amounts of Ethereum and seemingly consistent connections to EOS who are interested in manipulating the market … Whales in crypto make their own luck. with enough money, you can force the market in any direction you please”











































































































