 Hackers target Trezor crypto wallet users after mailing list got compromised
Hackers target Trezor crypto wallet users after mailing list got compromised Hackers target Trezor crypto wallet users after mailing list got compromised
A malicious actor used social engineering to access an internal tool used by newsletter delivery service Mailchimp.

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
Hardware cryptocurrency wallet manufacturer Trezor has divulged that its customers are being targeted by so-called “phishing” attacks after Mailchimp, the firm’s email automation service provider, was “compromised by an insider targeting crypto companies.”
“We are currently investigating how many customers might have been affected following an insider compromise of a newsletter database hosted on Mailchimp,” Trezor wrote in a blog post today, adding:
“The Mailchimp security team disclosed that a malicious actor accessed an internal tool used by customer-facing teams for customer support and account administration. The bad actor gained access to this tool as a result of a successful social engineering attack on Mailchimp employees.”
Status update on the ongoing phishing attack:https://t.co/IXq1I3Y1i7
— Trezor (@Trezor) April 4, 2022
Keep your app close, keep your seed phrase closer
Further, the attacker is specifically targeting crypto-related companies, Trezor noted. As a result, its wallet users began receiving phishing emails on Sunday, April 3, asking them to click a link that leads to the download page for a “Trezor Suite lookalike app.”
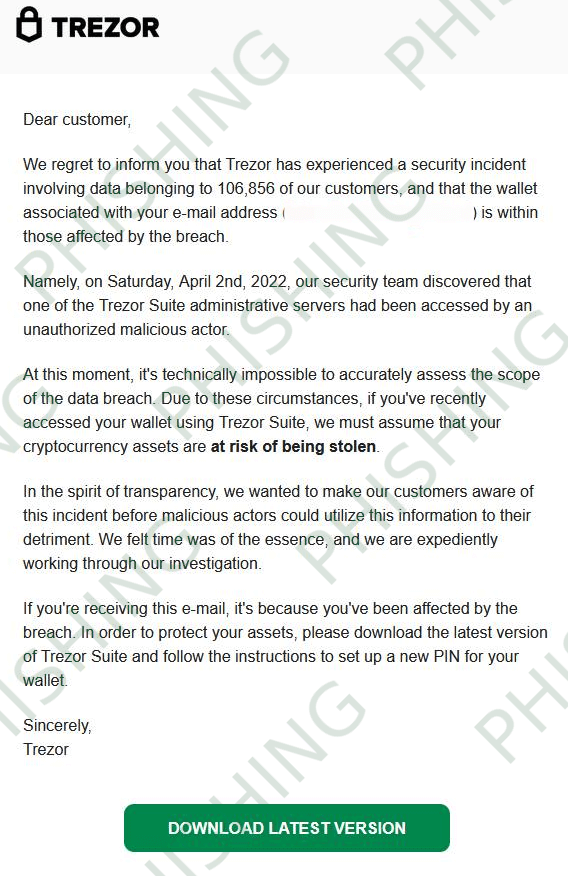
If an unsuspecting user falls into this trap, the malicious app then asks for their seed phrase—basically the private key that gives the perpetrators full access to their crypto holdings. Once entered, the seed gets compromised and users’ funds are immediately transferred to the attackers’ wallet.
“This attack is exceptional in its sophistication and was clearly planned to a high level of detail. The phishing application is a cloned version of Trezor Suite with very realistic functionality, and also included a web version of the app.”
MailChimp have confirmed that their service has been compromised by an insider targeting crypto companies.
We have managed to take the phishing domain offline. We are trying to determine how many email addresses have been affected. 1/
— Trezor (@Trezor) April 3, 2022
Luckily, since potential victims have to actually install the malware on their devices (although there is also a web version), contemporary operating systems should alarm them about its unknown source. “This warning should not be ignored, all official software is digitally signed by SatoshiLabs,” Trezor pointed out.
Stay vigilant
According to Trezor, the firm has already shut down the phishing domain. However, if some users have entered their seed phrases after all, they should immediately move their crypto to a newly generated address (unless it’s already too late, of course).
“If you have not received such an email, there is still a chance your email address has been leaked, so it is best to remain vigilant in case a new wave of emails appear. Compromised email addresses may be targeted again in future so please report any new phishing attempts directly to [email protected].”
Until this issue is resolved, the wallet manufacturer has ceased any newsletter activity. Additionally, users should “not open any emails appearing to come from Trezor until further notice” and make sure they are using anonymous email addresses for “Bitcoin-related activity,” the firm urged.





































































































