 SushiSwap token allocation exploit drains $3.3M as users urged to revoke token allowances
SushiSwap token allocation exploit drains $3.3M as users urged to revoke token allowances SushiSwap token allocation exploit drains $3.3M as users urged to revoke token allowances
SushiSwap Head Chef Jared Grey has confirmed a bug in the RouterProcessor2, yet 190 ETH has reportedly been recovered

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
A critical vulnerability has been identified in the DeFi protocol SushiSwap by security firm PeckShield this weekend, with the exploit involving the ‘RouterProcessor2’ contract used for trade routing on the SushiSwap exchange.
“It seems the SushiSwap RouterProcessor2 contact has an approve-related bug, which leads to the loss of >$3.3M loss (about 1800 eth) from 0xSifu,” PeckShield posted on Twitter. SushiSwap head developer Jared Grey confirmed the issue, urging users to revoke permissions for all contracts on SushiSwap as a security measure. The bug has resulted in a loss of over $3.3 million, primarily affecting a single user, 0xsifu, known in the Crypto Twitter community.
Grey stated,
“Sushi’s RouteProcessor2 contract has an approval bug; please revoke approval ASAP. We’re working with security teams to mitigate the issue.”
The exploit appears to have impacted users who approved SushiSwap contracts within the last four days, according to DefiLlama developer 0xngmi. Meanwhile, security teams continue to investigate the issue, track stolen funds, and work to recover affected assets.
Recovery of funds
“Recovery efforts are underway,” said Jared Grey, citing a tweet from MetaSleuth that provided a breakdown of the stolen funds. The first attacker, 0x9deff, returned 90 ETH of the 100 they had stolen, while BlockSec rescued 100 ETH and pledged to return it shortly. Negotiations between sifuvision.eth and c0ffeebabe.eth are in progress, with most stolen funds traced to “beaverbuild, rsync-builder, and Lido: Execution Layer Rewards Vault.”
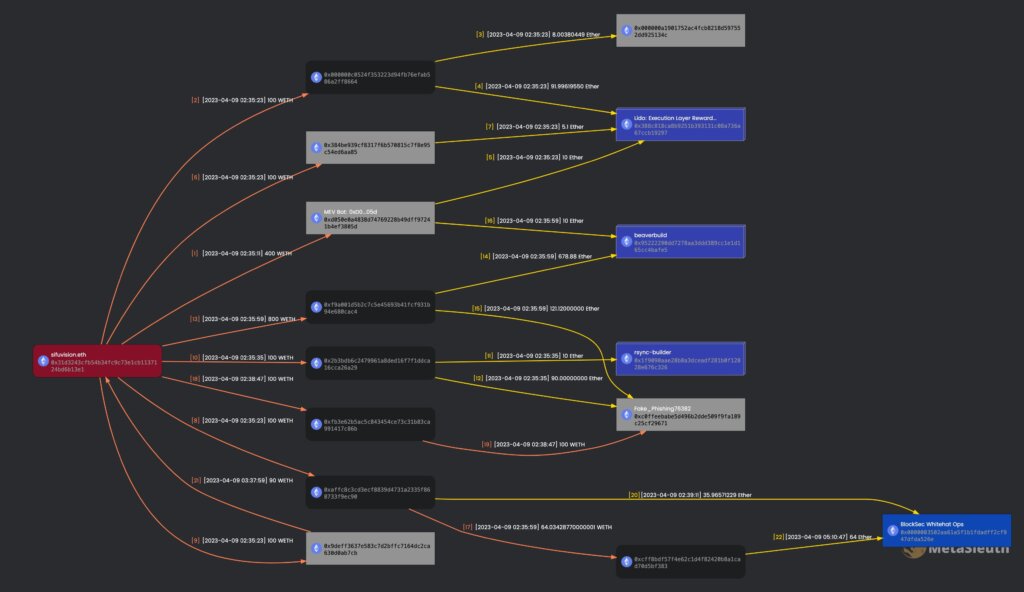
BlockSecTeam acknowledged their involvement in the recovery efforts, tweeting,
“We knew that @SushiSwap RouteProcessor2 was attacked. We evaluated possible damages in the past few hours and made this public only after we think it’s safe: users’ assets are always our first priority. Btw: we rescued part of them and will release the details later.”
As developers and security teams continue to address the vulnerability and recover lost funds, users are strongly advised to revoke permissions for all SushiSwap contracts to protect their assets.
The incident underscores the importance of ongoing vigilance and security measures within the DeFi ecosystem, as the growing sector remains vulnerable to exploits and attacks targeted to the misconfiguration of accounts.
As of press time, the Sushi token is down 4.9% on the day, trading around $1.08.









































































































