 Crypto ransomware payments fall 40% in 2022
Crypto ransomware payments fall 40% in 2022 Crypto ransomware payments fall 40% in 2022
Ransomware payments fell $309M in 2022 from a high of $766M in 2021 as victims refuse to pay OFAC sanctioned attackers

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
Funds collected by ransomware attacks fell to $456.8 million in 2022 from a high of $765.6 million in 2021, according to a new report from analytics firm Chainalysis.
Crypto-related ransomware attacks have seen a steep fall in success rate over the last 12 months.
Crypto ransomware activity
The chart below shows the rise and fall of funds acquired through ransomware attacks over the past 6 years. A dramatic increase was seen in 2020 as stolen funds hit $765 million, with 2021 seeing similar amounts stolen by bad actors.
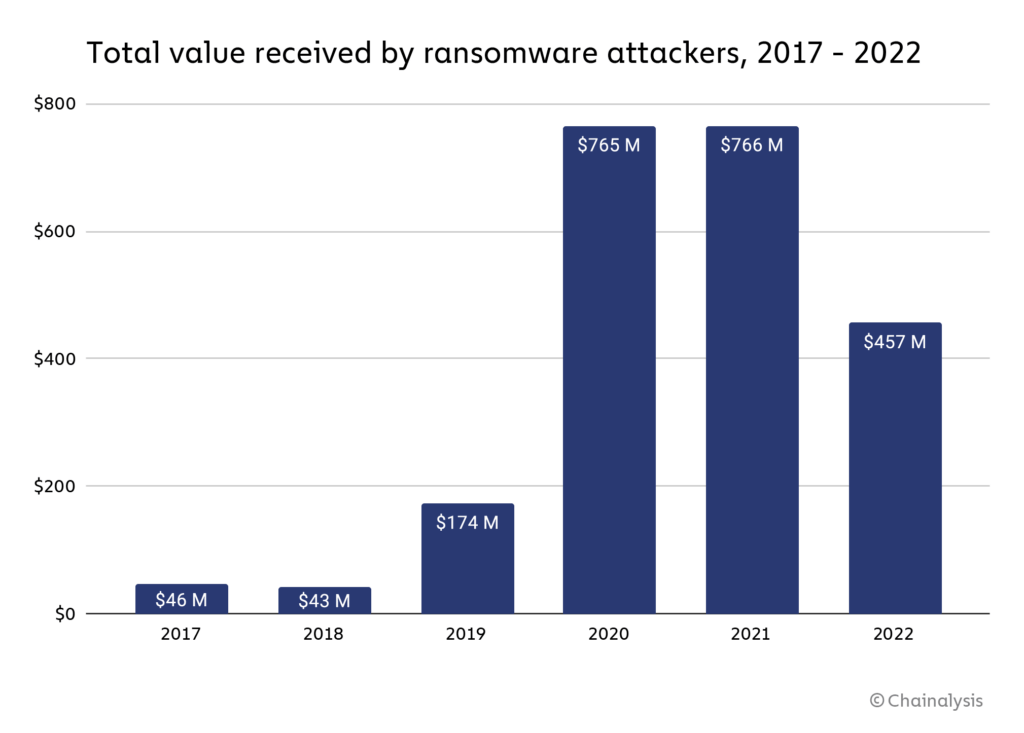
While the Chainalysis report recognized that “the true totals are much higher” as it is likely that there are addresses owned by ransomware attackers that have not yet been identified, the fall indicates victims are becoming wise to such attacks. As a result, Chainalysis made a statement supporting this sentiment.
“[Ransomware payments falling] doesn’t mean attacks are down… We believe that much of the decline is due to victim organizations increasingly refusing to pay ransomware attackers.”
Ransomware Strains explode
Although payments to remove ransomware have fallen dramatically, the number of ransomware strains exploded in 2022. A strain is a type of ransomware with common variants: Royal, Ragnar, Quantum, Play, Hive, and Lockbit.
Fortinet, a leading cybersecurity hardware and software company, reported over 10,000 unique strains active throughout 2022.
Strains have a decreasing lifespan as bad actors continue to vary attack vectors to optimize the volume of stolen funds. For example, in 2012, strains lasted 3,907 days, while in 2022, the average length was just 70 days. As a result, cybersecurity solutions must keep up with an increasing number of active strains in their defense strategy.
Ransomware funds
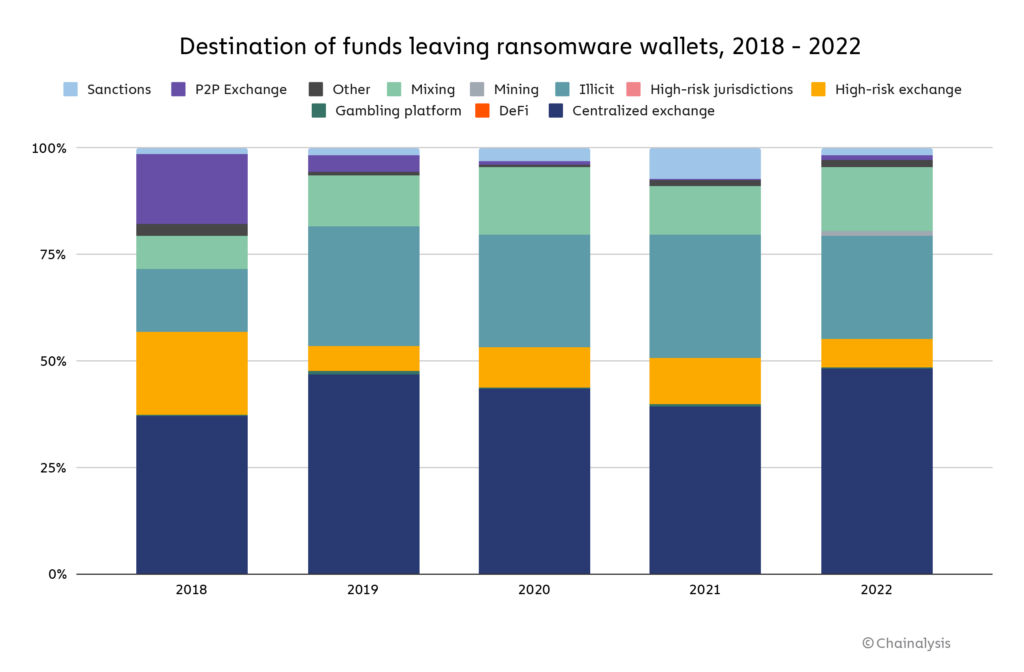
Funds acquired through ransomware attacks are laundered through several avenues. The majority of funds are still sent to popular centralized exchanges. However, P2P exchanges, a popular solution for ransomware attackers in 2018, now make up a tiny percentage of the overall volume.
After centralized exchanges, a persistent method of laundering funds is using darknet markets designated as ‘illicit’ in the Chainalysis chart below. Finally, mixing services make up the next most significant portion, allowing attackers to ‘wash’ crypto with little recourse from global authorities.
On-chain data forensics
Chainalysis used on-chain data to identify “affiliate” markets for ransomware software whereby third parties receive a “small, fixed cut of the proceeds” in a ransomware-as-a-service model.
“We can think of it as the gig economy, but for ransomware. A rideshare driver may have his Uber, Lyft, and Oja apps open at once, creating the illusion of three separate drivers on the road — but in reality, it’s all the same car.”
On-chain data has allowed companies like Chainalysis to trace bad actors across the blockchain and possibly identify the next attack vector. For example, Conti, a prevalent ransomware strain, was disbanded in May 2022. Yet, on-chain data has revealed that wallets connected to Conti are now moving onto other strains such as Royal, Quantum, and Ragnar.
Ransomware attackers “re-used wallets for multiple attacks launched nominally under other strains,” making tracing activity relatively elementary.
Decline in ransomware payments
The number of successful ransomware attacks fell due to the increased understanding of the landscape, improved security measures, and better on-chain forensic capabilities. As a result, victims are refusing to pay attackers, as many are linked to OFAC-sanctioned parties.
In 2019 just 24% of victims refused to pay, whereas, in 2022, the percentage increased to 59%. Paying a ransomware bounty to a party on the OFAC sanctions list could now be “legally riskier.” Allan Lisk, an intelligence analyst at Recorded Future, told Chainalysis;
“With the threat of sanctions looming, there’s the added threat of legal consequences for paying [ransomware attackers.]”
The consequences of not paying ransomware demands can often devastate the victims, who often lose access to essential data. However, as the illicit industry becomes less financially viable, the hope is that the number of attacks also falls, thus reducing the number of victims.
Regardless, the role of cryptocurrency in ransomware attacks is clear. It is a method to steal hundreds of millions of dollars worth of crypto each year. However, that is not to say that there isn’t more lost to traditional financial assets, many of which are not traceable through a blockchain.





































































































