 Zcash Powers of Tau Privacy Ceremony Successful — The Secret Process Behind Zcash
Zcash Powers of Tau Privacy Ceremony Successful — The Secret Process Behind Zcash Zcash Powers of Tau Privacy Ceremony Successful — The Secret Process Behind Zcash

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
Zcash is one of the first cryptocurrency to build privacy into a blockchain-based currency. This privacy is derived from a mysterious process called “The Ceremony.”
How Bitcoin Handles Privacy

People think that Bitcoin is anonymous. Yet, it has come to light that there is little privacy on the Bitcoin network. Although Bitcoin addresses are pseudo-anonymous, it is possible for someone to analyze the Bitcoin ledger and deduce the identity of people using their transaction history.
By linking addresses and transactions together, law enforcement officials and criminals could deduce the identities of Bitcoin users.
The Man Behind Zcash

Zooko Wilcox, a Colorado-based security specialist, was an early contributor to the Bitcoin protocol.
He recognized the privacy deficiencies in Bitcoin and wanted to improve upon it.
According to Wilcox in a podcast on NPR, the biggest strength of Bitcoin is also a substantial weakness regarding privacy:
“One of the strongest factors of Bitcoin, it’s transparency, could also put people’s privacies at risk.”
This was a deal-breaker for Wilcox who believes that privacy is a necessary human right:
“[Privacy is a] necessary condition for the exercise of free choice, morality, intimacy, and political participation.”
Unfortunately, building such features into Bitcoin in 2016 would prove near-impossible with the community’s resistance to modify the core protocol. However, Wilcox was convinced that a digital currency with the decentralization of Bitcoin and privacy of cash is possible. From that idea, Zcash (Zero Cash) was born.
The Mechanics Behind Zcash
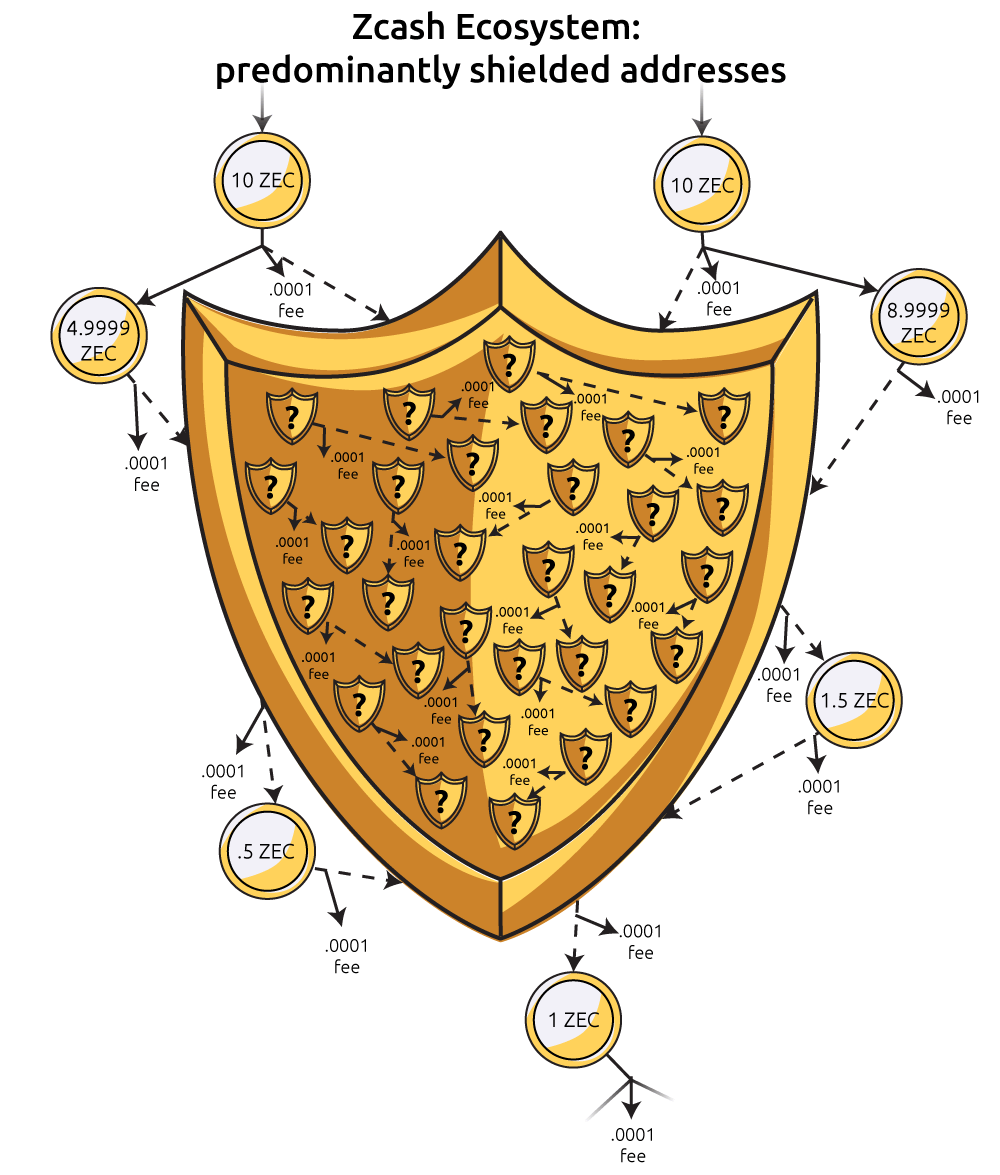
Zcash uses Bitcoin’s core code and improves upon the anonymity aspect of transactions. Zcash utilizes a cryptographic method known as “zero-knowledge proofs,” which leverages complex mathematics to prove a piece of information is true without revealing anything about that underlying piece of information.
These zero-knowledge methods are baked into the Zcash protocol as zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) and enable most of the security features that characterize Zcash.
The most important feature is “shielded transactions.” A shielded transaction is the term for a private transaction using zk-SNARKs on the Zcash network.
Unlike other methods by cryptocurrencies to provide user privacy, shielded addresses look identical to observers of the Zcash blockchain allowing for unprecedented levels of transaction privacy in 2016.
The Catch to zk-SNARKs
However, zk-SNARKs comes with a catch. Implementing the system has a huge vulnerability, at least at inception. The security of zk-SNARKs is predicated on a seed, an enormous randomly generated number, that must remain secret to ensure the security of the protocol.
If someone were to uncover the key that zk-SNARKs are built upon, then that person could mint millions of Zcash out of thin air.
However, even if the key were compromised the privacy of the system would remain intact. Every shielded address on the system is protected “solely by mathematics (modern encryption) and do not rely on anything else for their privacy.”
The Privacy Ceremony that Makes it Possible
For Zcash to succeed, it is imperative that the way the key is generated is trustable and transparent. For such a herculean feat, Wilcox concocted the plan to conduct:
“the most secure and most sophisticated cryptographic ceremony that has ever been performed.”
The Sprout ceremony, the privacy ceremony to initialize Zcash, was scrutinized to the smallest detail. The founding team wanted to ensure every possible security risk was taken into account and wanted to prove the process was untainted to the public. To do so here are a few precautions the team made:
- Filmed every portion of the ceremony and released it to the public.
- Filmed the filming equipment to prove that the first set of equipment wasn’t tampered with.
- Purchased new computers for the sole purpose of generating the key.
- Generation of the key was split over six participants to reduce the risk that all six of them were compromised.
- All mediums, computers, and memory which interacted with the key were dismembered, destroyed, and burned.
For additional details on the Sprout ceremony, check out this NPR podcast done in collaboration with the Zcash founders.
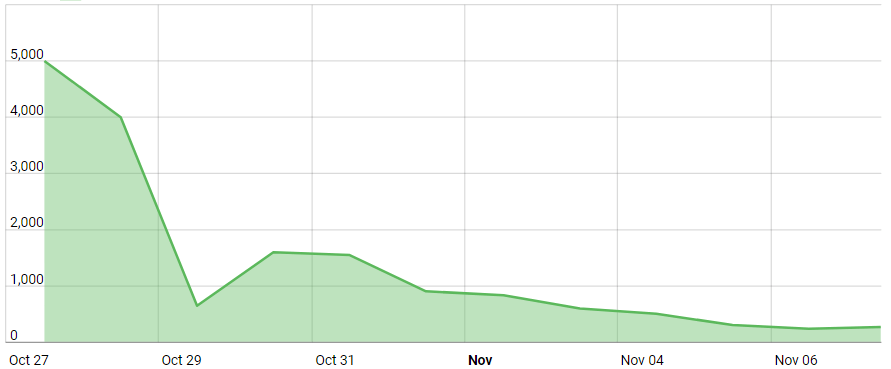
When Zcash launched on October 28th, it was sensational. The first cryptocurrency to implement a strong privacy component to a blockchain. Following launch day the price of a single Zcash peaked at $5,300 when Bitcoin was trading at less than $720.
The Privacy Ceremony 2.0
Recently, the Zcash team successfully conducted a second ceremony: the “Power of Tau” privacy ceremony. The second ceremony upgraded many of the security features in the Zcash protocol.
However, unlike the first ceremony, the Powers of Tau was open to the public and included hundreds of participants across the globe.
The Power of Tau ceremony was similar to the Sprout ceremony, but the process was improved to allow the inclusion of a scalable number of participants. As described by the Zcash Foundation:
“You can think of this process as a bit like shuffling a deck of cards in public. Each participant shuffles the deck, proves that they did not modify or add any of the cards, and then hands the deck to the next participant.”
Additionally, the more participants in the ceremony, the more secure the process becomes. Unlike the Sprout ceremony where the onus of proof was on the six members who generated the key, in an open system:
“As long as one participant successfully destroys their randomness when they’re finished, the resulting parameters are secure. As more and more participants are added, it becomes unlikely that an adversary could have compromised everyone.”
Each of these participants is then able to attest to the successful completion of the process.
Upgrades to the Zcash Protocol
With the Power of Tau successfully implemented there were a few notable improvements to Zcash.
- Security features in Zcash now require much less computation. Previously, a huge amount of computing and memory power was necessary to conduct Zcash shielded (term for the protocol’s private) transactions, which limited its use on the network.
- The Power of Tau ceremony will become the primary updating process for the protocol, allowing for a more transparent and trustworthy process for updating Zcash.
Controversy Surrounding zk-SNARKs Usage
A controversy surrounding Zcash is the limited use of the protocol’s private transactions. Many users do not know how to enable zk-SNARKs on the network, or the other hoops to jump through are too onerous for a typical user.
The reduction in computational intensity should make use a little more widespread. However, if there is still an insufficient userbase for shielded transactions, then the security of the whole system is harmed.
According to official Zcash website, the more people who enable the security feature, the more secure the network is as a whole. Ideally, more than 50% transactions on the network would use zk-SNARKs which would help obfuscate the identity of other visible transactions on the network.
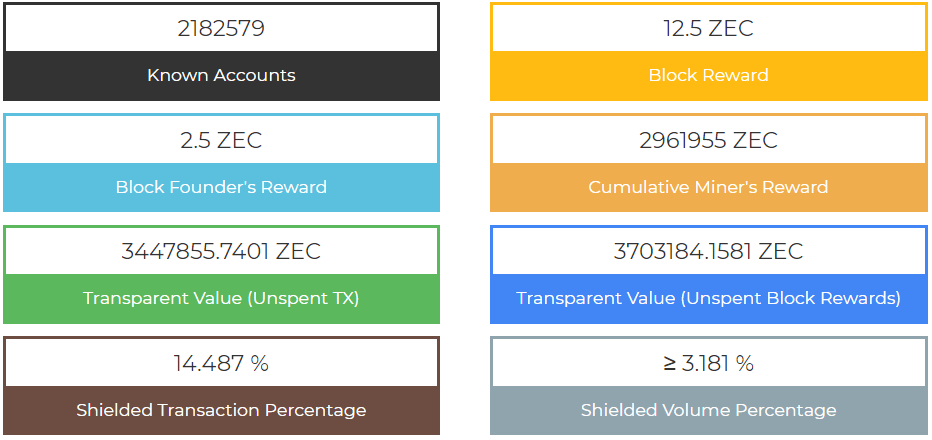
However, when a smaller percentage of users utilize shielded addresses, then “it’s relatively trivial to assume that shielded addresses on average have a higher balance, making them a higher target for attempts at theft.” On top of that, a hacker could use network timestamps from unshielded transactions to deduce the identity of shielded transaction users.
Currently, only 14% of Zcash transactions are shielded
Conclusions on the Zcash Cryptocurrency
Zcash is one of the first cryptocurrency to implement completely private transactions successfully. Not only that, the Zcash team is still on the cutting-edge of digital currency privacy with many other cryptocurrencies following their lead.
Even with the deficiencies of Zcash, future Power of Tau ceremonies will continue to enhance the security and efficiency of the Zcash network.
For more information about Zcash including price, market cap, technical information and social media links, please see our Zcash coin profile or read our post entitled “Introduction to Zcash (ZEC) – Zero-Knowledge Cryptography.”














































































































