 Ethereum vanity address exploit may be cause of Wintermute hack
Ethereum vanity address exploit may be cause of Wintermute hack Ethereum vanity address exploit may be cause of Wintermute hack
It may take less than 2 months to brute force hack an Ethereum vanity address using a GPU mining rig.

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
The Ethereum community is reviewing the nature of the recently announced $160 million Wintermute hack and has stumbled upon a potential attack vector. One of Wintermute’s addresses has the properties of a vanity address which could be the root of the vulnerability.
wintermute's address had 7 leading 0's
according to @k06a's estimation, can brute for this in 50 days using 1000 GPUs
the attacker was definitely a pro pic.twitter.com/JNOQ3qdXiV
— tuba 🦈 (@0xtuba) September 20, 2022
Vanity addresses are generated cryptographically by assigning a specific prefix or suffix to a program that then generates potentially millions of addresses until it finds one matching the specified conditions.
One such tool — Profanity — is available via GitHub and has had serious security concerns for some time. The repository is abandoned due to “fundamental security issues in the generation of private keys,” according to the readme.md file.
A blog post by the 1inch team is included in the markup, which lists several potential vulnerabilities in the code. Although the codebase has allegedly been updated to remove “all affected binaries,” the methodology may be flawed at its core.
According to research from k06a, a contributor to 1inch, 0xtuba was able to calculate that it may take only 50 days to brute force an address with seven leading 0s using 1,000 GPUs. Given Ethereum’s recent move to proof-of-stake, plenty of miners are currently looking for somewhere to apply their GPU power.
The image below showcases the estimated time to generate an Ethereum address with seven leading 0s using an RTX 3070TI GPU home gaming computer.
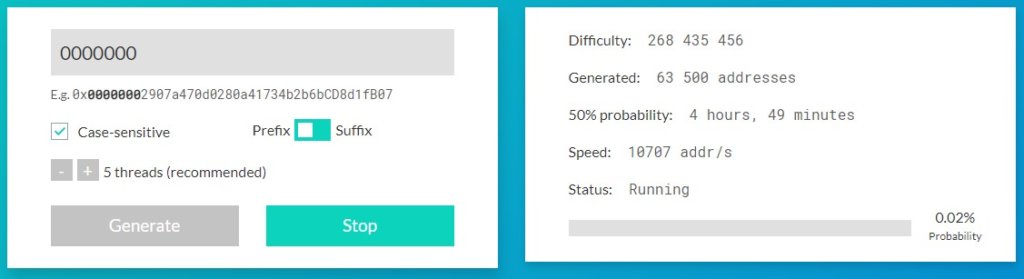
Should this attack vector be confirmed viable, there is now a fear that some miners may choose to move toward malicious means to ensure their farms continue to return a profit.
The 1inch blog post contains the following warning:
“Notice: Your money is NOT SAFU if your wallet address was generated with the Profanity tool. Transfer all of your assets to a different wallet ASAP! “
CryptoSlte has reached out to Wintermute for comment on the method used to generate addresses but has not immediately received a response.
Update Sept. 20, 3:40 PM BST: Crypto security company Certik has released additional information confirming suspicions of an exploit through Profanity.
Here is what we know so far from the @wintermute_t exploit 👇
We have recorded that $162,509,665 have been stolen.
The exploit is likely due to a brute force attack on Profanity wallet compromising a private key.
Stay vigilant! pic.twitter.com/zVRd3e5TbS
— CertiK Alert (@CertiKAlert) September 20, 2022


 CoinGlass
CoinGlass 


 Farside Investors
Farside Investors 
















































































