Sturdy Finance halts market after $800,000 exploit linked to faulty price oracle
Sturdy Finance halts market after $800,000 exploit linked to faulty price oracle Sturdy Finance halts market after $800,000 exploit linked to faulty price oracle
Blockchain security firm BlockSec stated that Sturdy Finance suffered a reentrancy attack alongside its price oracle manipulation.

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
Sturdy Finance paused its markets on June 12 following a protocol exploit – losses are estimated at around 442 ETH ($800,000) per Peckshield.
In a statement, the team confirmed it was aware of the exploit, adding that no additional funds are at risk and no user actions are needed currently – with more information to follow pending investigation results.
Sturdy Finance has yet to respond to CryptoSlate’s request for additional comments as of press time.
Blockchain security firms explain how Sturdy Finance was exploited
Blockchain security firm Peckshield initially reported that Sturdy Finance’s exploit was linked to a faulty price oracle. Further analysis showed “the root cause [was] due to the defective price oracle to compute the cB-stETH-STABLE asset price.”
Web3 knowledge graph protocol 0xScope corroborated this report, adding that the hacker transferred the stolen funds to crypto-mixing protocol, Tornado Cash, and the Change Now exchange.
Meanwhile, smart contract auditor BlockSec noted that in addition to the oracle price manipulation reported by Peckshield and 0xScope, the exploit also showed signs of a “typical Balancer’s read-only reentrancy” attack.
Using the attack transaction hash, BlockSec explained how the attacker first borrowed over 100,000 staked Ethereum from Aave in a flash loan before exploiting a liquidity pool managed by Sturdy Finance’s team on the Balancer.
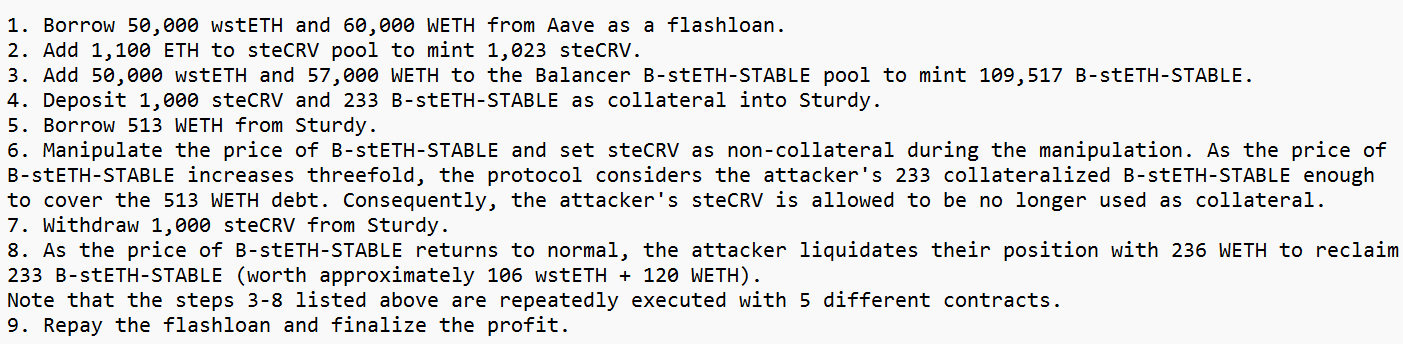
According to CertiK, a reentrancy attack allows an attacker to drain funds of a vulnerable contract by repeatedly calling the withdraw function before it updates its balance.




 Arkham Intelligence
Arkham Intelligence 

 Farside Investors
Farside Investors 
 CryptoQuant
CryptoQuant 
 CoinGlass
CoinGlass