A silent security scandal or dying profession? DeFi Bug Bounty Wall of Shame has millions in unpaid bounties
A silent security scandal or dying profession? DeFi Bug Bounty Wall of Shame has millions in unpaid bounties A silent security scandal or dying profession? DeFi Bug Bounty Wall of Shame has millions in unpaid bounties
Lack of accountability in DeFi bug bounty programs amplifies the need for transparency and trust.

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
The crypto community is grappling with issues surrounding bug bounty programs, a crucial mechanism for discovering and addressing system vulnerabilities.
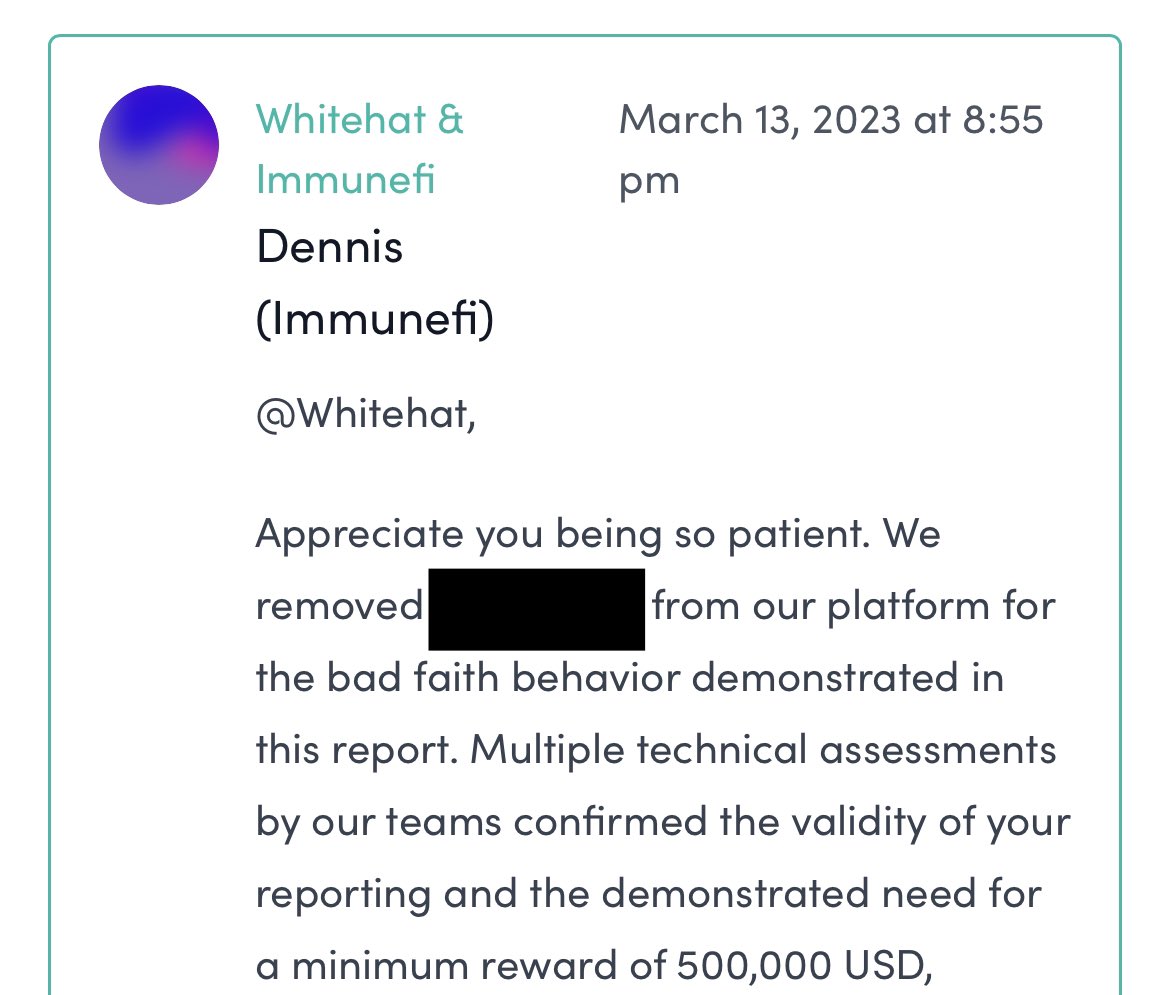
Usmann Khan, a web3 security auditor, posted on Aug. 17, “Remember that projects can simply not pay, whitehat,” with a screenshot of a message from Immunefi indicating a project had been removed from its bug bounty problem for failure to pay a minimum of $500,000 in bounties.
In response, security researcher Marc Weiss shared the ‘Bug Bounty Wall of Shame’ (BBWoS), a list documenting unpaid rewards allegedly owed to white hat hackers in web3. The data from BBWoS appears to signal a significant lack of accountability and trust within the crypto ecosystem that cannot be ignored.
The BBWoS indicates that a bug bounty for the Arbitrum exploit of Sep. 2022 had a $2 million reward. Yet, the white hate was awarded just $780,000 for identifying an exploit that exposed over $680 million.
Further, BBWoS states the CRV borrowing/lending exploit on Aave from Nov. 2022 led to the loss of $1.5 million, with $40 million at risk, and no bounty was paid to the white hat who identified the attack path “days before.”
Lastly, in April this year, just $500 was paid to a white hat who reportedly identified a way for managers to steal up to $14 million worth of “tokens from users using malicious swap paths” after being told by dHEDGE that the issue was “well-known.”
The list was created by whitehat hackers “tired of spending sleepless nights finding bugs in protocols only to have a payout of $500 when the economic damage totals in the millions,” with the creator stating,
“I created this leaderboard to help inform the security community as to the projects that don’t take security seriously so we can avoid them and spend time on the projects that do.”
The need for in-house auditors in DeFi.
In his presentation at the DeFi Security Summit in July, Weiss highlighted auditors’ critical role at various stages of protocol development. By integrating auditors and researchers in-house, he stressed their potential to make insightful architectural decisions, design effective codebases, and adopt a security-focused approach to protocol development.
Consequently, it is concerning when platforms fail to acknowledge and adequately reward the efforts of these security professionals when working on a contract basis.
Auditors Gogo and MiloTruck highlighted that non-payment for identified vulnerabilities is a widespread issue. Their posts underscore the urgent need for these platforms to enhance their accountability and trustworthiness and ensure due recognition for white hat hackers.
More transparency is required in handling vulnerabilities. High-profile cases listed on BBWoS, like the compromised deposit contract of Arbitrum, the economic exploit of Aave, and the malicious swap paths in dHEDGE, amplify this need.
Trusted Execution Environments in DeFi.
In response to Weiss’s issues about trust, Danny Ki from Super Protocol emphasized the potential of “decentralized confidential computing” to bolster trust in Web3 projects and mitigate vulnerabilities. Ki is referencing the option to run DeFi in Trusted Execution Environments (TEE), something inherent in Super Protocol.
A TEE is a secure area of a processor that guarantees code and data loaded inside be protected for confidentiality and integrity. However, one disadvantage of using TEEs within DeFi dApps is relying on proprietary architecture from centralized companies such as Intel, AMD, and ARM. There are efforts in the open-source community to develop open standards and implementations for TEE, such as Open-TEE and OP-TEE projects.
Ki argues that should “Web3 projects operate within confidential enclaves, there may be no need to pay out for vulnerabilities, as the security will be inherently fortified.”
While a fusion of blockchain and confidential computing could provide a formidable security layer for future projects, the move to replace bug bounties and security auditors with TEEs seems complex, to say the least.
Issues with bug bounties in DeFi.
Still, there are additional concerns for white hat hackers, such as improper bug disclosures from security firms on social media. A post from Peckshield identifying a bug in July simply said, “Hi @JPEGd_69, you may want to take a look,” with a link to an Ethereum transaction.
Gogo lambasted the post stating, “If this vulnerability were responsibly disclosed instead of exploited, PEGd’s users wouldn’t have lost $11 million, No reputational damage would have been caused, The guy would have gotten a solid bug bounty instead of been front-run by an MEV bot.”
Gogo shared their bug bounty experience with Immunefi, a company they described as ‘beyond fantastic,’ where the payout required a mediation process, eventually leading to a satisfactory payout of $5k for a critical bug.
These insights from the web3 security community underscore the critical role of auditors and the importance of effective bug bounty programs to the crypto ecosystem’s security, trust, and growth.
As some have identified, hacks are covered extensively in the news and on X, but what for those who discover the exploits and are never adequately compensated? Nearly $2.5 million in allegedly unpaid bounties is listed on BBWoS alone, yet, as Ki highlighted, could the future include a web3 that is innately secure with no need for bounties?



 Farside Investors
Farside Investors 


 CoinGlass
CoinGlass