Crypto money laundering drops nearly 30% in 2023 as cyber criminals change tactics
Crypto money laundering drops nearly 30% in 2023 as cyber criminals change tactics Crypto money laundering drops nearly 30% in 2023 as cyber criminals change tactics
Sophisticated crypto criminals are adapting their money laundering strategies and exploiting services like crypto mixers and cross-chain bridges.

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
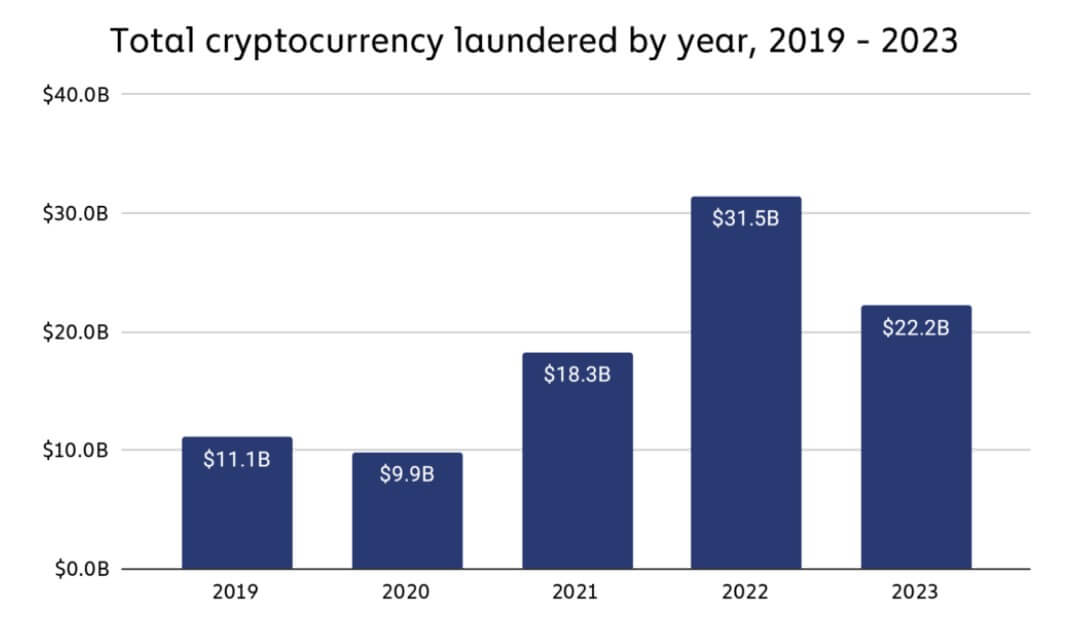
Crypto money laundering experienced a significant decline of 29.5% in 2023 compared to the previous year, primarily due to a decrease in overall crypto transaction volume.
According to a Chainalysis report, illicit addresses moved approximately $22.2 billion in digital assets to various crypto services in 2023, marking a notable drop from the $31.5 billion transferred in 2022. This decline aligns with a 14.9% decrease in legitimate and illegal crypto transaction volumes.
Centralized exchanges remained the primary destination for funds from illicit addresses, although there was a noticeable increase in criminal fund movements toward gambling services and bridge protocols.
In detail, 109 exchange addresses received over $10 million each from illicit sources, totaling $3.4 billion in 2023, a significant rise from the $2 billion received by 40 addresses in 2022. Similarly, 1,425 exchange addresses received over $1 million each, amounting to approximately $6.7 billion in 2023, compared to $6.3 billion across 542 addresses in 2022.
Meanwhile, funds from illicit addresses to bridge protocols surged from $312.2 million in 2022 to $743.8 million in 2023.
‘Changing tactics’
Chainalysis noted that sophisticated crypto criminals with on-chain laundering skills, like the infamous North Korean-backed hackers Lazarus Group, are adapting their money laundering strategies and exploiting new services like crypto mixers and cross-chain bridges.
For context, the regulatory pressure on crypto mixing services like Sinbad and Tornado Cash, forced Lazarus Group to shift its money laundering strategy to YoMix, a new mixing service provider.
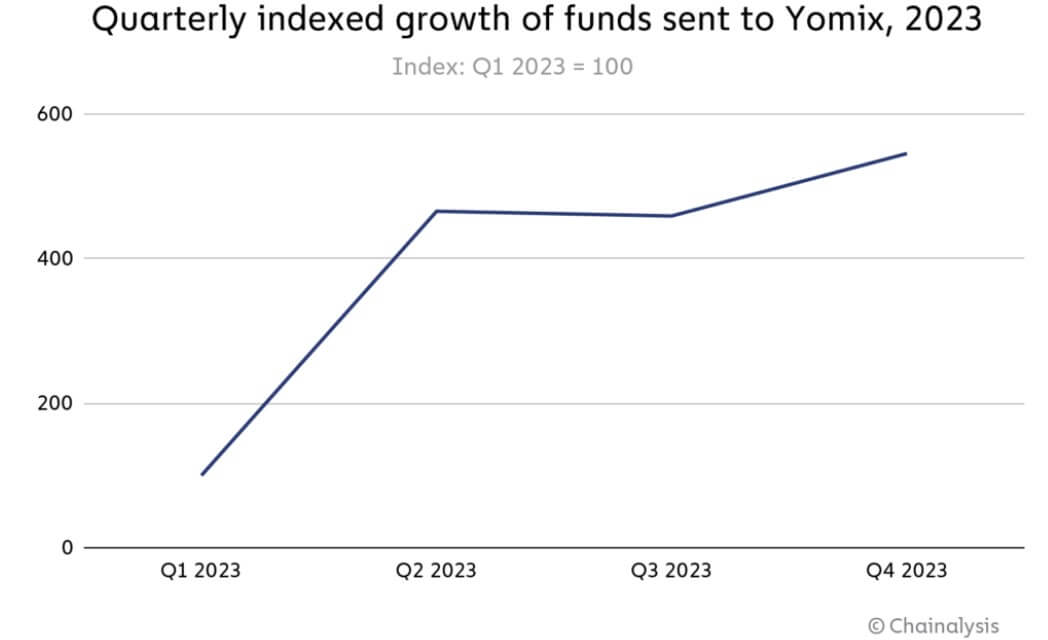
According to Chainalysis, this transition led to a notable increase in YoMix’s activity for last year, with its inflows rising more than fivefold. Additionally, nearly one-third of YoMix’s inflows can be traced back to wallets associated with crypto hacks.
“The growth of YoMix and its embrace by Lazarus Group is a prime example of sophisticated actors’ ability to adapt and find replacement obfuscation services when previously popular ones are shut down,” Chainalysis concluded.
In addition, North Korean-backed hacker groups were observed to be among the most common crypto criminals that utilized cross-chain bridges for money laundering activities.