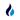BatchOverflow Exploit Creates Trillions of Ethereum Tokens, Major Exchanges Halt ERC20 Deposits
BatchOverflow Exploit Creates Trillions of Ethereum Tokens, Major Exchanges Halt ERC20 Deposits BatchOverflow Exploit Creates Trillions of Ethereum Tokens, Major Exchanges Halt ERC20 Deposits

Photo by Taras Shypka on Unsplash
A newly-discovered Ethereum smart contract exploit has resulted in the generation of billions of ERC20 tokens, causing major exchanges to temporary halt ERC20 deposits and withdrawals until all tokens can be assessed for vulnerability.
The exploit, termed the batchOverflow exploit, was first observed on the 22nd of April, when 115 octodecillion BEC (Beauty Coin) was created in two transactions. At the time, BEC was trading at $0.32 per token, which makes the total dollar value of the exploit around $3.7 novemdecillion, a truly absurd figure, which is a 1 followed by 60 zeros.
The cryptocurrency community at large only became aware of the exploit on the 24th of April, however, when the same exploit was used on the Smart Mesh token to generate over $5 octodecillion USD in tokens.
Exchanges Shut Down ERC20 Functionality
Several major exchanges have completely shut down ERC20 token deposit or withdrawals subsequent to the transactions. Hong Kong-based exchange OKEx, the third largest cryptocurrency exchange in the world, announced the suspension of all ERC20 token deposits in an official blog post on Tuesday:
We are suspending the deposits of all ERC-20 tokens due to the discovery of a new smart contract bug – “BatchOverFlow”. By exploiting the bug, attackers can generate an extremely large amount of tokens, and deposit them into a normal address. This makes many of the ERC-20 tokens vulnerable to price manipulations of the attackers.
The OKEx team continued to explain that the exchange will be suspending the deposits of all ERC20 tokens until “the bug is fixed” in order to “protect public interest.” OKEx isn’t the only exchange to completely halt ERC20 token deposits due to the exploit, however.
Poloniex recently posted a Tweet that announced the temporary suspension of ERC20 deposits and withdrawals while the batchOverflow bug is investigated.
We've temporarily suspended ERC-20 token deposits and withdrawals while we review all smart contracts for exposure to the reported batchOverflow bug. We take any reports of vulnerabilities very seriously to ensure that customer funds remain safe. Thank you for your patience!
— Poloniex Exchange (@Poloniex) April 25, 2018
Popular instant cryptocurrency exchange platform Changelly has followed suit, stopping all ERC20 transactions until a security check is performed. Unlike traditional exchanges, Changelly acts as a broker and doesn’t require users to possess accounts or Changelly-hosted wallets in order to exchange crypto.
Dear Customers, ERC20 tokens are temporarily unavailable due to an exploit check. We will bring them back, once we are sure there is no vulnerability in deposits received. Follow the updates! https://t.co/qYutri4X3X
— Changelly.com (@Changelly_team) April 25, 2018
Huobi Pro has also issued an announcement, stating that abnormal SmartMesh transactions observed resulted in the suspension of deposits and withdrawals. The statement also included a reference to a transaction conducted by the party behind the Smart Mesh batchOverflow exploit, noting that the Huobi Pro system detected the deposits and did not credit them.
What is the BatchOverflow Exploit?
The impact of the batchOverflow exploit was first made public by blockchain security startup PeckShield, who detected an unusual MESH token transaction on the 25th of April. According to PeckShield, the smart contract used in the exploit possesses a classic integer overflow problem.
An explanation of the exploit provided by PeckShield sheds some light on the above example:
“As shown … both _fee and _value are input parameters which could be controlled by the attacher. If _fee + _value happens to be 0 (the overflow case), the sanity checks in line 206 could be passed. It means the attacker could transfer huge amount of tokens to an address (line 214) with zero balance. Also, a huge amount fee would be transferred to the msg.sender in line 217.”
PeckShield have since provided a full list of ERC20 tokens that are affected by the exploit, which include:
- MESH
- UGToken
- SMT
- SMART
- MTC
- FirstCoin
- GG Token
- CNY Token
- CNYTokenPLus
The implications of the exploit on the ERC20 standard are obvious — the Ethereum platform touts the effectiveness of smart contracts as “code is law,” but the fact that there is no traditional security response mechanism in place to prevent these kinds of attacks from occurring is concerning indeed.
Market Response
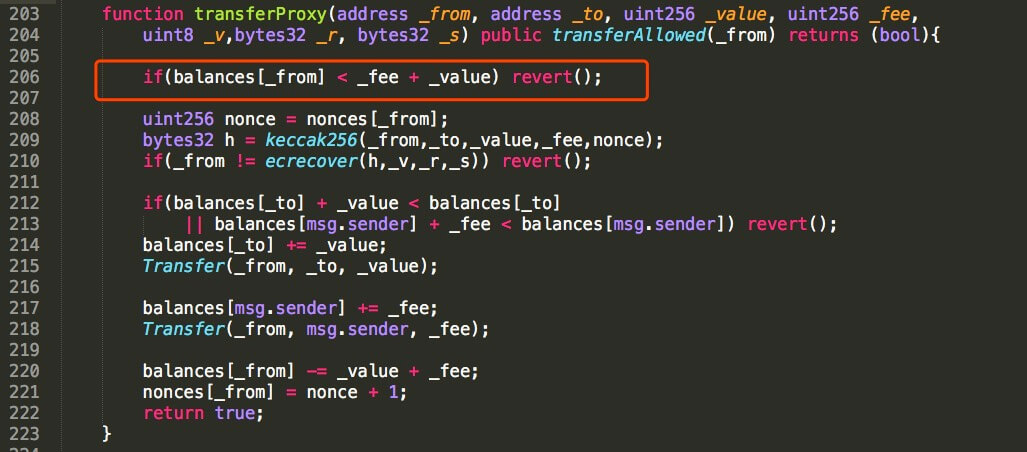
The cryptocurrency market, which is currently struggling through a correction of this week’s significant positive momentum shift, has responded negatively to news of the exploit. Smart Mesh token values took a significant hit at the time of the exploit announcement, falling from $0.11 to $0.08 in less than one hour.
Ethereum also took a relatively significant hit at the time of the exploit announcement, falling from $664 to $612 over the course of the day as the market absorbed the news. As exchanges announced temporary security measures regarding the exploit and the root cause of the issue was identified, however, ETH value has recaptured lost ground, rising back up to $630.
Not-So-Smart Contracts
While the party behind the exploit has been unsuccessful in this specific case, the presence of this exploit in the market is a clear sign that the extremely broad spectrum of ERC20 tokens — some of which boast per-token values that are not easy to dismiss — must be more rigorous with the manner in which smart contract functionality is implemented.


 CoinGlass
CoinGlass 


 Farside Investors
Farside Investors