How YFI competitor Pickle Finance was exploited for $20m in Ethereum stablecoins
How YFI competitor Pickle Finance was exploited for $20m in Ethereum stablecoins How YFI competitor Pickle Finance was exploited for $20m in Ethereum stablecoins

Photo by Reka Biro-Horvath on Unsplash
Call it a hack or call it an exploit, yesterday an unknown attacker managed to drain $20 million from an Ethereum-based yield aggregator called Pickle Finance into their own address.
This attack was quite different and much more complex than the previous DeFi exploits, though, leaving some to ask if it was an inside hack.
What is Pickle Finance?
Pickle Finance was launched in the midst of the foodcoin craze of the summer, during which developers were releasing both absurd food projects and cool projects with food branding (Yam, for instance). Pickle fell into the latter category.
At first, it launched as a way to try and manipulate the price of off-peg stablecoins back to their peg: the protocol would offer more in farming rewards to cheaper stablecoins and would offer less to the stablecoins that were over the dollar peg.
It seemingly worked, with MakerDAO‘s DAI, which was trading at $1.03 or $1.04 at the time, inching down toward $1.02.
Since these origins, Pickle Finance has become a yield aggregator project, similar to Yearn.finance (YFI).
A yield aggregator is a project that finds the best yields projects have to offer, then optimizes deposits to maximize yield.
The hack
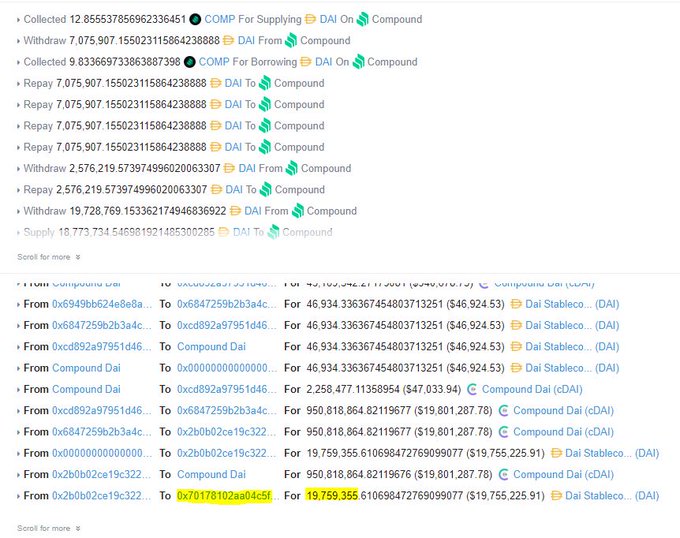
Around mid-day yesterday, users began to notice a suspicious transaction involving Pickle’s pDAI Jar, or the strategy through which DAI earns yield farming rewards.
Dashboards indicated that the Jar was emptied for $20 million, though with no announcement or admins on the Discord, Twitter, or Telegram at the time, there was confusion as to what happened.
It was quickly posited that it was an attack: the user who made this suspicious transaction had nothing to do with the Pickle Finance Deployer, and also funded their account with 10 ETH from Tornado Cash, a mixer that obfuscates the origins of Ethereum.
Initial analysis of the attack was light; this one was much more complicated than previous attacks, which involved flash loans and price manipulation. This one seemed to have exploited flawed parts of Pickle’s code in an extremely clever manner.
After theories flew about for a number of hours, users began to notice something suspicious about the swapExactJarforJar function in the Pickle Finance controller contract.
Smart contract engineer Emiliano Bonassi explained that what the attacker did is deploy an evil Jar that looked like the original one, then swapped the funds in the original Pickle Finance Jar into their own. There was no check that prevented this swap function from being used by a non-admin/governance address and no check that the Jar being swapped to was one approved by the governance/timelock.
Further analysis was done by Vasa, a blockchain engineer and writer.
Hayden Adams, founder of Uniswap, responded to the incident by stating that it’s good to remember that “‘complicated’ defi hacks are still super avoidable.” He added that what’s important is that devs put a lot of “love and effort into user security.”
It’s good to remember that “complicated” defi hacks are still super avoidable.
Just requires putting a lot of love and effort into user security.
Expensive audits help but are a red herring.
The people best equipped to make a system secure are the devs who build it. https://t.co/E6JnPeDVRd
— Hayden Adams ? (@haydenzadams) November 22, 2020
Pickle Finance developers have advised all users to withdraw funds for the time being, as there are fears that the exploit is repeatable with the millions left on the platform.