Mining pools used by criminals to funnel stolen funds into exchanges – report
Mining pools used by criminals to funnel stolen funds into exchanges – report Mining pools used by criminals to funnel stolen funds into exchanges – report
Cyber criminals are using mining pools as mixers to launder illicit funds, making it look like their tainted funds are mining proceeds.

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
On June 15, Chainalysis reported that cybercriminals are exploiting mining pools to mix their criminal proceeds with freshly mined cryptocurrencies.
The report pointed to a highly active deposit address at a mainstream crypto exchange. This wallet received a large number of cryptocurrencies from both mining pools and wallets linked to ransomware.
The address received a staggering $94.2 million worth of cryptocurrency, of which around 20%, or $19.1 million, came from ransomware-linked wallets. The address also received $14.1 million from mining pools.
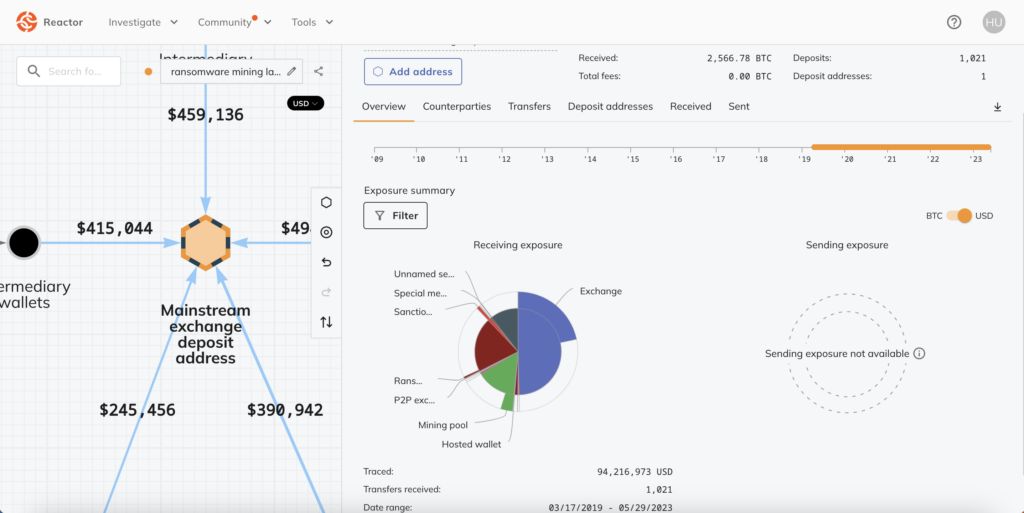
Chainalysis found that both the ransomware wallet and the mining pool address sent funds to the exchange deposit wallet via intermediaries. However, in some cases, the ransomware wallet also sent funds directly to the mining pool.
This tactic is a “sophisticated attempt at money laundering,” Chainalysis said. The bad actors funnel funds to the exchanges through mining pools to create the illusion that the tainted funds are mining proceeds rather than linked to cybercrime. Therefore, the criminals are using the mining pools as a crypto mixer to avoid triggering alarms at the exchange.
This is a growing trend — Chainalysis found 372 exchange wallets that have received funds from mining pools and at least $1 million from ransomware-linked wallets. In total, these exchange addresses have received $158.3 million from ransomware wallets since 2018.
Scammers are also using mining pools to launder funds
Scammers are also employing the same tactic as ransomware attackers. For instance, funds linked to the BitClub Network scam, in which over $700 million was stolen, were mixed with Bitcoin obtained from a Russia-based mining operation in 2019, as per Chainalysis.
Moreover, the wallets on the exchanges also received funds from BTC-e, a defunct Russian crypto exchange. BTC-e was shut down in 2017 for facilitating the laundering of funds, including those linked to the Mt. Gox hack.
The criminals allegedly commingled funds from BitClub, BTC-e, and the Russian mining operation to obfuscate the origin of funds. The report stated,
“We believe it’s possible that the money launderers in this case purposely mingled funds from BitClub and BTC-e with those gained from mining in order to make it look like all of the funds sent to the two exchanges came from mining.”
Since 2018, such exchange addresses have received nearly $1.1 billion from scam-linked wallets. Additionally, such exchange wallets have received at least $1 million from mining pools during the period.
To combat this growing issue of illicit funds, Chainalysis suggests that mining pools and hashing services should implement strict wallet screening and know-your-customer procedures. Mining pools should verify the source of funds and reject all deposits from illicit addresses, it said.
Chainalysis’ full report is available here.



 Deribit
Deribit