Kaspersky Labs Warns Against Cryptocurrency Mining Malware Affecting Several Corporations
Kaspersky Labs Warns Against Cryptocurrency Mining Malware Affecting Several Corporations Kaspersky Labs Warns Against Cryptocurrency Mining Malware Affecting Several Corporations

Photo by Thomas Lefebvre on Unsplash
The public threat of cryptocurrency miners seemingly increases daily. In the latest instance, a cryptocurrency miner dubbed “PowerGhost” was found to have infected servers of entire corporations, extracting massive amounts of energy to fulfill unlawful purposes.
Miner Threatens Corporations
As stated on SecureList on July 26, 2018, Moscow-based Kaspersky Labs revealed the presence of a new miner malware after its global software systems raised security alarms across several clients.
Called “PowerGhost,” the miner is said to have stealthily installed itself on a victim P.C. and deploy across workstation servers and corporations to gain their computing resources for mining cryptocurrencies.

Hackers deploying mining software are becoming increasingly sophisticated and implement various tactics to avoid getting flagged. These include running additional software to slow down the speed of CPU fans, switching off mining software during a users’ “active” hours, and artificially showing “low” computing power usage – all of which assist illegal mining software to go unnoticed, subsequently leading to increased profits for the attackers over time.
Interestingly, such illicit mining, or “cryptojacking” as popularly known, is reportedly replacing traditional cybercrime tactics such as ransomware, as per data collated by an earlier Kaspersky report.
Stealth Mode
In the “PowerGhost” instance, hackers deployed a “fileless technique” by delivering malware over a “clean” software, outside the purview and suspicion of system administrators.
PowerGhost utilized a PowerShell script to deliver the base code, containing the illicit miner, msvcp120.dll, and msvcr120.dll operation libraries and a protective, “shell” code for hiding the exploit.
The program was found to use several file-less techniques for remaining undetected by the users and antivirus software. Notably, the virus was infected by remote administration tools such as Windows Management Instrumentation.
For the infection process, the running PowerShell script automatically downloaded the mining code and immediately launched it for use, regardless of writing on the victim’s hard drive.
DDoS Attacks and Affected Countries
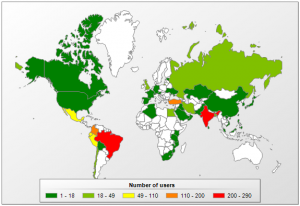
Amongst the several discovered PowerGhost instances, Kaspersky additionally noticed DDoS codes in some versions, indicating the attackers aimed to make extra money by DDoSing computer networks.
Although targeted at both individuals and companies, the attack’s inherent delivery system made it easier to spread within a company’s local area network. The chart below shows the extent of PowerGhost attacks:
As observed, the virus was encountered most in Brazil, Columbia, Turkey, and India.