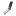Ledger Reveals Five Vulnerabilities in Competitor Trezor’s Wallets
Ledger Reveals Five Vulnerabilities in Competitor Trezor’s Wallets Ledger Reveals Five Vulnerabilities in Competitor Trezor’s Wallets

Cover art/illustration via CryptoSlate. Image includes combined content which may include AI-generated content.
Ledger, a major crypto hardware wallet manufacturer based in France, revealed five security vulnerabilities found in the Trezor Model T and Model One, major competitors to the Nano Ledger.
Ledger’s Attack Lab Discovered Vulnerabilities in Trezor’s Hardware Wallets
The market for cryptocurrency hardware wallets is a rather competitive one due to the nature of cryptocurrencies. As a result, many companies are looking to create products that satisfy the strict security needs of the technology.
Ledger, a major hardware wallet manufacturer based in France, has been one of the few companies that put its research labs to good use. Apart from hacking into their own devices, the company uses its Attack Lab to expose security vulnerabilities in competitors’ devices.
According to the company’s blog post, Ledger contacted Trezor to share five vulnerabilities that were discovered by its Attack Lab. Ledger gave the company a “responsible” disclosure period to fix said vulnerabilities.
After failing to address four of the five bugs found even after two extensions, Ledger went public with its findings in a Mar. 11th blog post. At the recently-held MIT Bitcoin Expo in Boston, Ledger’s chief security officer also presented some of the ways in which Trezor’s wallets could be hacked.
French Wallet Manufacturer Lists Five Different Ways Trezor Wallets Can be Hacked
Ledger’s study found several weaknesses in the Trezor One and Trezor T wallet. The first problem the company identified was how easily the devices could be faked. The devices could be entirely imitated, as they are both made with generic, (relatively) accessible components.
The device’s tamper-proof sticker can be easily removed, allowing attackers to compromise original devices bought directly from Trezor and then return them, seemingly untouched.
Then, Ledger’s Attack Lab was also able to guess the PIN on both the Model T and Model One by using a “side-channel attack,” which is hacking using information (typically) gained from information revealed by the hardware as it processes information, such as timing information, power consumption, or even sound.
By calculating how much power was used by the device as it verifies pins, the lab was able to correctly guess the pin in less than five attempts. This is the only issue the company managed to solve in its 1.8.0 firmware update.
The third and fourth vulnerabilities Ledger found could both be solved by replacing the device’s core component with a “Secure Element chip,” as opposed to the current computer chips used in the devices. Researchers also found that an attacker who has physical access to Trezor One and Trezor T can easily extract all the data stored within the flash memory of the device.
Finally, Ledger found that the crypto library does not contain proper countermeasures against software attacks aside for its “Scalar Multiplication function,” a core cryptographic operation used in cryptocurrency, particularly for signing transactions.
However, the function alone isn’t enough to protect against physical side-channel attacks. While Trezor has previously claimed both the Model T and the Model One are resistant to such attacks, Ledger found that an attacker with physical access to the device can extract secret keys through these methods.
Update: Trezor has posted a response in the form of a blog post to the accusations from Ledger.



 Farside Investors
Farside Investors 


 CoinGlass
CoinGlass